Journalists are working harder than ever to protect their sources. As public records requests become less effective at the U.S. federal and state levels, journalists have had to rely less on those records and more on whistleblowers from within government agencies or the organizations that receive government funding.
At the federal level, the government has capriciously closed FOIA requests, shut down FOIA offices, and avoided FOIA compliance by marking communication as sensitive. The government has also closed off its own mechanisms for public accountability by firing inspectors general, cutting the budget for the National Archives and Records Administration, and ignoring the Presidential Records Act.
Forced to turn to insider sources, journalists find government workers are increasingly afraid to speak because of the fear of retribution. As ProPublica reporter Sharon Lerner recently observed, “So many of the avenues for federal employees to seek justice or address retaliation have been shut down.”
In this environment, SecureDrop is more important than ever. As a secure communication platform to connect whistleblowers to journalists, SecureDrop advances press freedom when it becomes more accessible to more newsrooms and easier for journalists to use. Here is how we are making those improvements, all while safeguarding whistleblowers’ anonymity against ever-evolving threats.
SecureDrop Workstation
The SecureDrop Workstation officially left the pilot stage last year, and our main focus this year has been improving its usability and reliability. We enabled the use of thousands of printer models by switching to driverless printing and improved our printing UI so newsrooms can more easily get hard copies of documents whistleblowers submit. We removed Whonix in favor of vanilla Tor, resolving a regular pain point for our users during updates. Our users will find workstation installation simpler without manually verifying signing keys and with the securedrop-admin tool as a Debian package.
Behind the scenes, we’ve also been migrating our testing infrastructure from a custom solution to OpenQA, which enables us to easily test multiple scenarios and even simulate user interactions employing the same infrastructure we apply for testing the Qubes operating system on which the workstation is built.
This year, the SecureDrop team made the decision to rewrite the existing journalist app from scratch, allowing us to incorporate lessons learned from the pilot into a new architecture and to use a framework that’ll allow us to make future improvements faster. After half a year of work, the SecureDrop app is feature-complete and will be released after it undergoes a security audit in early 2026. More details to come in future blog posts, but for now, here’s a quick teaser:
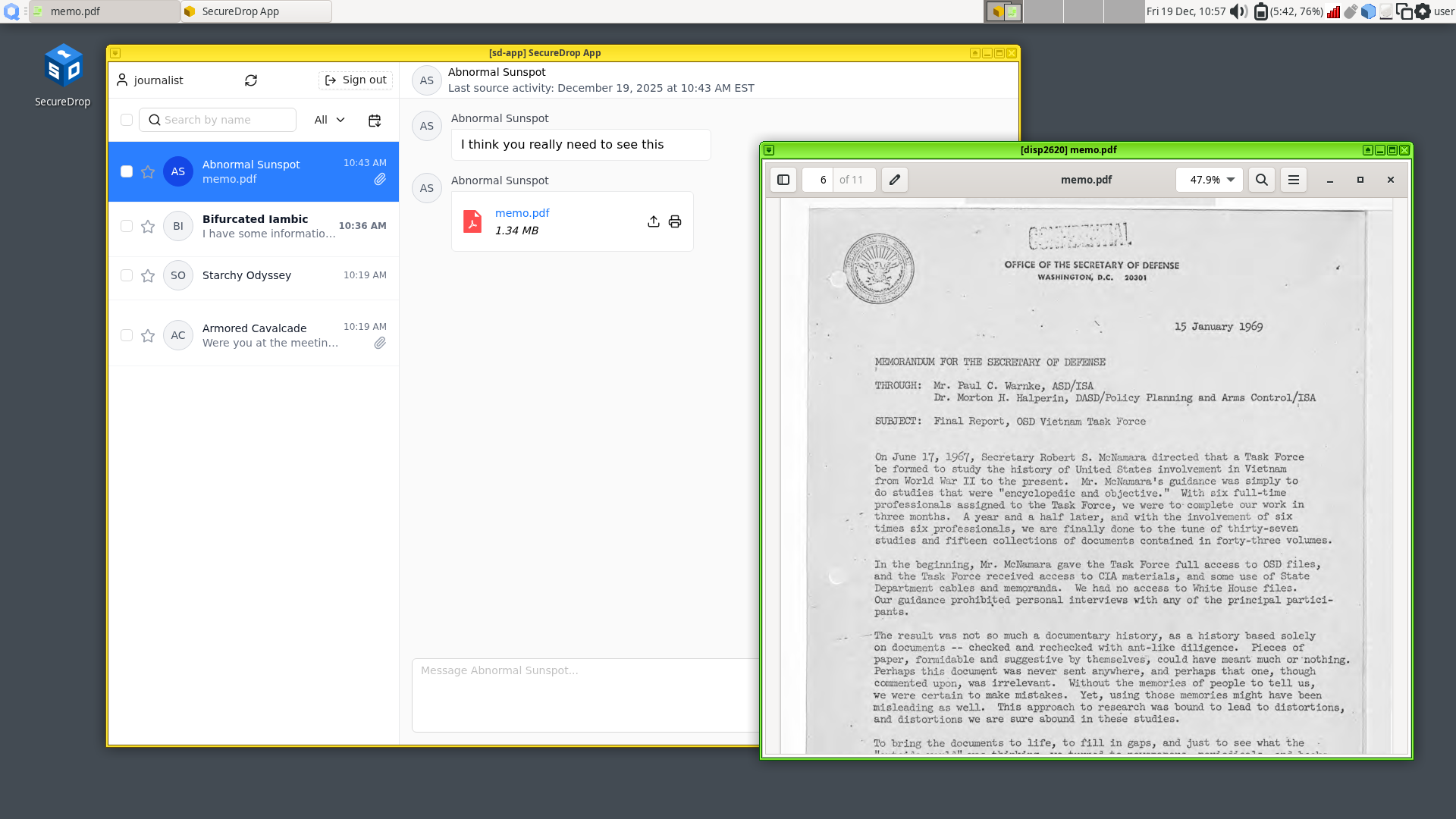
SecureDrop server
The SecureDrop server continues to be a stable and secure platform for sources and journalists to use. This year, we invested significant time in preparing and rolling out a fully automated migration to upgrade the server operating system from Ubuntu Focal (20.04) to Ubuntu Noble (24.04). Unlike past migrations that required downtime and full reinstalls of every server, most 2025 upgrades did not require any manual action, saving newsroom administrators time.
To support the new SecureDrop app for journalists, we’ve rewritten the synchronization API from scratch, making it faster and more efficient. While not yet released, it will be enabled on servers once the app is available early next year.
Next generation of SecureDrop
Further out on the horizon, we are attacking a long-standing problem with browser-based cryptography. With the evolving WEBCAT project, we will make possible the cryptographic verification of code and end-to-end encryption as a standard, not just for newsrooms running SecureDrop but across the entire web.
This capability will enable us to bring even higher security to SecureDrop, via the new SecureDrop Protocol for end-to-end-encrypted messaging between sources and journalists. Together with researchers at ETH Zurich, we are working to prove the protocol’s security properties for publication in a peer-reviewed journal.
We said goodbye to our previous VP of Engineering Erik Möller this year, after seven years leading the team, and welcomed Dr. Jennifer Helsby, who rejoins FPF as the new chief technology officer. We also welcomed John Skinner, FPF’s new engineering manager, who now leads the SecureDrop team. Finally, Vicki Niu joined us as a senior software engineer.
As an open source project, SecureDrop is free to use by anyone — we don’t charge for it. But developing it isn’t cheap, especially as a nonprofit. If you’d like to support our work, please consider donating to the Freedom of the Press Foundation (FPF). And if you’re interested in or already using SecureDrop within your newsroom, consider reaching out about a priority support contract.





