
Photo by Thomas Jundt. CC BY-NC 2.0
Proton Mail is a Switzerland-based email client that offers end-to-end encryption between its users by default. This means that communication between anyone whose email is managed by Proton Mail can only be viewed by members of that party; No outside parties, including Proton Mail itself, can view the content of any messages sent through the service. Proton Mail uses PGP, Pretty Good Privacy, an encryption standard commonly used for encrypting the content of emails.
PGP is famously tricky to use, but through its design, Proton Mail simplifies things a great deal. If you’re already using a client like Mailvelope, Thunderbird, or Apple Mail with GPG Suite, you have a good basis for getting started. If you’ve never used PGP, or need a refresher on the fundamentals, have a look at one of EFF’s excellent explainers.
This guide takes you through how to safely and effectively use Proton Mail’s web app, which you access via your browser at https://mail.proton.me. Android and iOS apps are also available for mobile, and those with a paid account can use the Proton Mail Bridge to check your email from Thunderbird, Apple Mail, or your desktop email client of choice.
What’s the added value, anyway?
If you’re already curious about Proton Mail, then you are probably keenly aware that email communication can be spied upon. Let’s dig a little further into how and why that might happen.

A portion of a leaked slide from MUSCULAR, a joint U.S.-United Kingdom surveillance program, that highlighted where Google data centers lacked encryption at the time. Image via Wikipedia
Most email providers use a protocol called TLS, or Transport Layer Security, to securely deliver email between the sender and recipient’s servers. In the past, this was also called by its earlier protocol, SSL, or Secure Socket Layer, which TLS replaced. This makes sure that the minute you press send from your inbox, the email should not be eavesdropped on by anyone between your and your friends’ email providers. Ideally, the only people who can read the content of your email are you, your friends, and the email provider itself.
However, this is no longer a 100% assurance of your privacy. With increasing regularity, legal processes, like subpoenas, have coerced email providers into handing over users’ emails. And sometimes, encryption is simply undermined by incredibly resourced adversaries. Spooky!
For the privacy conscious, another type of encryption is required in order to protect against the consequences of a data request or technical vulnerability. This is where End-to-End Encryption comes into play. With E2EE, a message is turned into complete gibberish before it even leaves your computer and reaches your email provider. This scrambled text can only be unscrambled by your conversational partner. The email provider only holds onto the encrypted gibberish, and in the event of a warrant or subpoena, this gibberish would be the only content it could hand over. (Metadata is another story, but that’s a whole other post!)
This seems like a perfect way to keep a message confidential, and it almost is! The only hitch? All parties must have the same capability to encrypt and decrypt messages to one another before an E2EE line of communication can be initiated.
If you're using Proton Mail to email someone who is not on Proton Mail, you should assume the content is not end-to-end encrypted and can be read by third parties that helped deliver the message. This may be your conversational partner's email provider (e.g. Gmail) or internet service providers (e.g. Comcast) if the connection is not encrypted in transit.
In other words, your ability to have an end-to-end encrypted conversation depends on whom you’re emailing.
Proton Mail’s privacy matrix
Here’s a handy guide to get the most value out of Proton Mail and other end-to-end encrypted communication systems.
| If the sender is a... | If the recipient is... | TLS by default? | E2EE by default? |
|---|---|---|---|
| ProtonMail user | ProtonMail user | yes | yes |
| ProtonMail user | Gmail user | yes | no |
| ProtonMail user | Self-hosted email user | it depends | no |
| Gmail user | ProtonMail user | yes | no |
Setting up PGP
Before using Proton Mail to communicate with others, you should first take care to maximize your privacy and security. In Proton Mail’s settings, visit the “Encryption and keys” section, to take advantage of some advanced features.
Set up private keys
The current default security settings for new Proton Mail users is good, offering modern standards for encryption keys. If you created a Proton Mail account several years ago however, you may notice that you have an auto-generated RSA key of 2048 bits. You should replace your primary key with a stronger 4096-bit RSA key. Next to your email address, under “Email encryption keys,” click “Generate Key” to add a new key. When prompted, select the “Compatibility RSA 4096-bit” option.
Once your new key is generated, click the down-arrow next to your new key to expand your keys. Mark the new, stronger key, as your primary key by clicking the down-arrow under “Actions” and selecting “Make primary.”
Now is the perfect time to export a copy of your private key (which will require you to enter your Proton Mail password) and save it to a safe storage space, like a USB stick that you can keep reasonably safe. You can also export your public key in a similar manner, to upload it to key servers elsewhere on the web.
Take note that this is also where you can revoke your key if it is ever compromised, or generate new ones for whatever reason.
Enable PGP with everyone!
If you recall, you can exchange end-to-end encrypted messages with any other Proton Mail user without ever having to set anything up. However, you will definitely want to enable the same protection with non-Proton Mail users who use PGP through another means.
Navigate to the “Encryption and keys” section in your settings, and scroll down to “External PGP settings.” Be sure to set the “Default PGP scheme” to "PGP/Inline."
Adding public keys for contacts
Proton Mail allows you to add people’s PGP public keys to your address book. Navigate to your Contacts, and select an entry. Open the contact’s “Email settings” by clicking the gear to the right of their entry. Then click “Show advanced PGP settings.”
Next to “Public keys,” select “Upload” to upload your contact’s PGP public key. Once the key is imported, make sure to set the “PGP scheme” to “PGP/Inline” (and not MIME). You can additionally set Proton Mail to automatically sign and/or encrypt all messages to that contact going forward. Click “Save” so the changes take effect.

Encrypting messages
No matter what you hear, having a Proton Mail account does not mean all your email conversations are automatically E2EE. But there are certain indicators that tell you how secure your conversation is. While looking for and understanding the indicators may take some getting used to, before long, using Proton Mail will be as simple as using any other email service.
When you compose a message from the Proton Mail web app, the recipient field will indicate whether your conversation will be end-to-end encrypted.
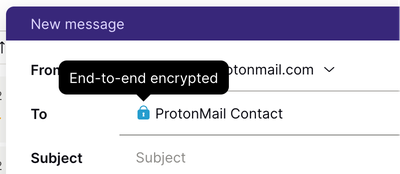
If you’re emailing someone who also uses Proton Mail, your messages will be end-to-end encrypted automatically. The recipient field shows a blue lock to the left of the address.
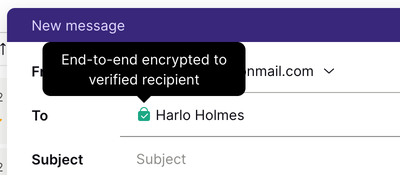
If you’re emailing someone who uses another service (Gmail, for example) and whose PGP key you have added into your contacts, your messages will also be end-to-end encrypted automatically. The recipient field shows a green lock to the left of the address.
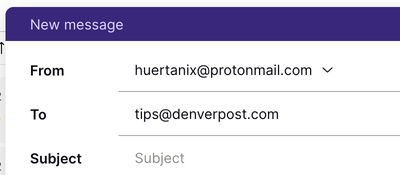
However, if you're emailing someone who uses another email provider, but you don’t have their PGP key added, end-to-end encryption is not possible. There won’t be any indication next to their address in the recipient field.
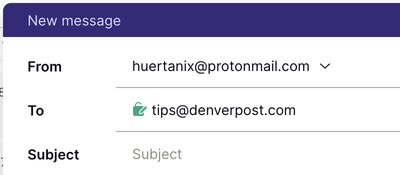
You may have opted in to having all your emails signed with PGP in your settings. Although this adds a cryptographic signature that could be used to verify the authenticity of your email, it’s important to note that this does not mean that it is end-to-end encrypted.
Keeping your account safe
As with any account you care about, you should take the time to safeguard it against certain threats. Not only do you want to make it harder for hackers to get into your account, but you also want to ensure you can access it if ever something goes wrong. Visit your settings to enable a few security features before using your account.
Set a strong, unique passphrase
When you reuse passwords, it only takes a breach of one service for hackers to figure out how to log in to all the other services you use.
This means you should be using a strong, unique passphrase. (Ideally, you should store this in a reputable password manager).
It’s especially important to have a backup of your password (e.g., backed up to a password manager), because if you lose your password, you will not be able to decrypt any of your old email ever again.
You may also set a reset/notification email address (such as your personal Gmail address) in the event you need to reset your password. However, you should take considerable care to lock down that backup email address as much as possible!
Set up two-factor authentication
Proton Mail currently supports two-factor authentication with one-time-use code apps like Google Authenticator or Authy. Follow the steps on the Proton Mail knowledge base to enable it and be sure to save your backup codes somewhere safe.
Monitor access
Proton Mail allows you to audit each connection your account makes with its servers. This allows you to do a few awesome things.
First, you can view all the IP addresses (locations) your account has been seen on, which is great for making sure it was you, and only you, who’s been in your Proton Mail account. In your settings in “Security and privacy,” under “Security logs,” and be sure to enable the “Enable advanced logs”.
Also, you can manage which sessions are currently active on your account, and revoke any session that is no longer needed, or suspicious, under “Session management”.
Take control of your privacy
Sometimes, hackers — or even advertisers — use sneaky tricks in email to pierce through your privacy, like tracking beacons embedded into images.
Sometimes these trackers are in images as small as one pixel, providing no value to you whatsoever.
Make sure Proton Mail only loads images and other remote content if, and only if, you request it. In your settings, hit ”Email privacy”. Make sure “Ask before loading remote content” and “Block email tracking” are both enabled.
Understanding the caveats
Proton Mail seems like the perfect solution for those who want to get started with end-to-end encryption over email without going down the rabbit hole when mastering PGP’s nuances. The Proton Mail team is diligent, attentive and responsive to surfaced vulnerabilities from the larger infosec community — an admirable quality everyone should look for when choosing a product. Like all products, however, there are some things to be aware of with Proton Mail before using it.
The backdoor spectre
Proton Mail is primarily accessed from its web interface. This means that every cryptographic calculation is handled in your browser, using code delivered from Proton Mail’s servers directly to you, each time you log in. In addition to trusting Proton Mail’s code, the security of your browser, and other factors, this also requires a strong amount of trust in Proton Mail as a company.
Security researchers have long pondered the possibility [PDF] that a company offering a web-based client doing in-browser crypto could be silently, but legally, compelled to deliver a backdoored version of their code to users specifically targeted by a FISA court order, or something similar. It has happened to users of other services before; one might call it “getting Lavabitten”.
On at least one occasion, Proton Mail has also been ordered to change some of its privacy practices. The company was compelled to log the IP address of one of its users, a French climate activist, after French authorities obtained the order from a Swiss court. This is different from compelling the disclosure of the content of your emails, but the principle matters: Proton Mail still must comply with lawful data requests.
Learning to use PGP with a client like GPG Suite, Thunderbird, or GPG4Win is a good option for journalists and other high-risks users who’ll want to keep these caveats — and an ever-changing threat landscape — in mind.
Some workflows might encourage risky user behavior

What happens if you want to send an end-to-end encrypted email to someone who doesn’t have a PGP key at all? Designing a proper workflow for encrypting messages to users who have no public key is a well-recognized challenge in security engineering. What Proton Mail (and a growing number of competing E2EE email services) does to address this is allow you to encrypt an email to your contact using a password that you are responsible for somehow sharing securely.
In this case, rather than the original content of the email, the email that lands in your contact’s inbox is a branded notification saying something to the effect of, “Click this link to view your message!!!” Your contact is then instructed to click through to a Proton Mail portal where they can view the original decrypted message after typing in your shared secret password.

In the digital security training space, trainers work very hard to teach people to identify this as phishing behavior. While it’s disheartening to see this UX pattern leveraged because that undermines the advice most likely to keep at-risk users safe, this is still a hugely convenient feature. Imagine being able to send personal details, like passport numbers, to a travel agent who is willing to go a tiny step further to protect your information, but not far enough to use PGP. It’s a classic example of the security and usability trade-offs companies must make. And remember, context is everything — always be wary of unsolicited emails enticing you to click through. When in doubt, ring someone up on the phone and have them confirm that they meant to send it!
Critiques aside, Proton Mail is an excellent choice for bootstrapping PGP-curious users onto more secure communications, and the company has implemented improvements that further demonstrate the product’s promise.



