Photo by Tracy. CC BY-NC-ND 2.0
Want to liven up any party? Come bearing gifts. While everyone else is giving traditional, physical gifts, we’ll be giving something much more exciting to our friends and family. We’ll give some simple security guidance, which I think we can all agree is better than another internet-connected kitchen appliance.
We work with news organizations on their digital security posture, and it turns out they use a lot of the same tools and practices everyone should use. Here are some ideas for gifts to make your next event more exciting.
The gift of understanding
We tend to think about computer and internet safety as an abstract concept. Instead, to think through the specific safety steps that are right for your friends and family, the most important thing we can do is ask specific questions.
- What do I want to protect? (e.g., the photos on my mobile device)
- Who do I want to protect it from? (e.g., a thief on the street)
- How likely is it that I will need to protect it? (Not at all likely? Very likely?)
- What will happen if I fail? (e.g., your most sensitive photos may be exposed)
- What am I willing to do to prevent these consequences? (e.g., password protect, and lock your phone screen in public)
We call this practice of thinking through our specific security concerns a risk assessment. The word ‘risk’ is important, because it communicates that information is not simply safe or unsafe. Instead, we can take steps to minimize risk and maximize safety, in a way that works for you.
One thing you may recognize right away is that risk is determined by your circumstances. Your idea about risk may change based on where you are located, how much you care about the consequences if things go wrong, and what you’re willing to do to prevent these bad outcomes.
You can begin to extend more concrete reasoning through risk assessments to other situations in your life, such as protecting your online accounts, physical devices, and your conversations.
Now your party is off to a good start.
The gift of account safety
How do websites and apps know who we are? We provide a username and password to prove it. Unfortunately, this is a brittle defense, but we can give ourselves more peace of mind by upgrading these defenses.
Don’t take the bait on phishing
You get an email from Facebook with notifications about an event you’d like to attend, later this week. You click a link in the email, and Facebook appears, asking for your password. But weren’t you logged in? Maybe it logged you out for some reason. You log back in.
What if it wasn’t Facebook? What if it was someone else, masquerading as Facebook?
A phishing page is a fake login page built to steal your credentials. Here’s how it works: someone sends you a message (e.g., via email or other channel) suggesting they are a familiar and trusted entity (e.g., Facebook). Typically they’ll forward a link to a fake login page, or a malicious file designed to give them unauthorized access to your data.
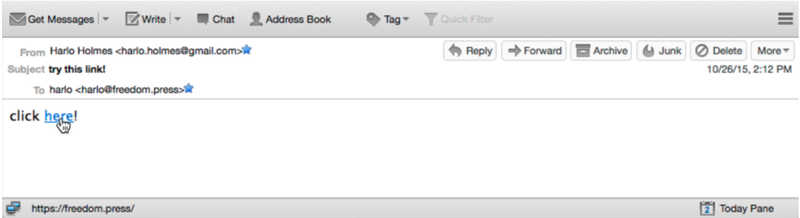
This is why it’s so important to double check that your email is coming from the right entity. Hackers will register domains that look similar to the domain they are targeting (e.g., accounts-facebook.com instead of facebook.com). If you’re not looking closely, you may miss the difference.
It’s also important to avoid using login links from emails, and to navigate to login pages from a more reliable source. If you’re going to click on a link, you want to ensure it’s going to the right place (e.g., by hovering your cursor and checking the URL).
When you share these tips at your next party, they’ll love it.
Learn how to identify several types of email phishing attacks.
Password reuse, and password managers
Because everyone has so many accounts, many people think it’s easier to just reuse passwords, or make small changes to your password on every website. This is a bad idea. Hackers know you reuse your password everywhere, so they only need to get one of your passwords to break into the rest of your accounts. (It seems like every week we hear about a password breach in the news.)
So we really want to use long, unique passwords on every website. At the same time, it’s also tough to remember a unique password for each of our accounts.
Password manager tools (e.g., 1Password) make it easy to remember only one password, while allowing you to use long, unique passwords for every website. Password manager will make your life both easier and more secure. How? You use one password to unlock your encrypted password “vault,” which securely stores your unique passwords, allowing you to access and automatically fill them out on all of your devices.
While a few password managers like 1Password, Bitwarden, and DashLane are all solid choices, they each have trade offs.
Learn more about choosing a password manager.
Two-factor authentication
On top of using unique passwords, one of the most important things we can do for account security is use more than a password.
Two factor authentication (2FA) strengthens logins by requiring a second piece of information, or a second “factor” beyond your password. This second factor is usually something you can access to prove who you are, but strangers are (hopefully) less likely to control, such as a temporary code delivered through your mobile device, or something on your body (e.g., a fingerprint).
There are a few popular ways to access 2FA, including codes delivered over SMS text messages, authentication apps (e.g., Google Authenticator, Authy, or Duo), as well as physical hardware devices, like a YubiKey, making it significantly more difficult for someone else to log in.

The gift of safer devices
Malware, updates, and installations
Malicious software tricks your computer into giving a third party unauthorized access, potentially letting them monitor your screen, keystrokes, microphone, or other features of your device. Malware typically works by exploiting holes in legitimate software.
So when Microsoft, Apple, and other software companies learn about vulnerabilities in their operating systems, teams of security researchers scramble to push out responsive software updates. The same is true for the apps that run on top of the operating system. Why? They’re racing against anyone who might want to misuse newfound vulnerabilities.
This is why you want to encourage others to update their devices, and the software that runs on top of it, as soon as updates are available.
The “cat and mouse” dynamic of the security industry also comes into conflict with our intuition about when and how to use software as ordinary users.
This leads us to download things all the time, just to try them. But the foundations for our software’s stability and safety are always shifting under our feet.
We should be honest with ourselves. Is this software — mobile game, social media platform, messaging service — something we need?
We can also avoid needless risk by choosing not to download unnecessary apps.
Even if we trust the applications that we install, if they go unused (read: if they don’t get active security updates), hackers will continue to discover vulnerabilities or exploits that could make them a liability. If you don’t need it, don’t put it on your device. And, if you don’t use it anymore, it’s time to delete it from your device.
Securing the data on your device
If your computer or mobile device is ever lost or stolen, it’s possible for thieves to copy data from your device’s storage. The good news is that it’s getting quite easy to enable disk encryption, which scrambles the data on your disk so no one can read it except for you. If you have a recent password-protected iPhone, your disk is already encrypted. Many Android devices are encrypted by default (check if yours is one of them), and enabling disk encryption is straightforward. On desktop devices you can also encrypt your disk drive using your operating system’s native software: FileVault for macOS, or BitLocker on Windows.
The gift of private conversations
You can also use encryption to secure your conversations with friends and family.
While regular text messages and voice calls could be monitored or recorded in a variety of ways, end-to-end encrypted messengers like the Signal app are designed to be available only to users in the conversation. Signal is open source, meaning anyone can look at its code, so security experts can confirm it works as promised. And, unlike most messaging apps, it retains no information about who spoke to whom, when and for how long.
Learn how to get started with Signal.
While these are all features we look in a messaging app, it only works if your friends and family use it as well. So make your next big celebration an opportunity to assist someone in getting started.
Give each of these gifts generously. You’re sure to be invited back next year to entertain everyone with more security wisdom.