
Many journalists are taking advantage of their home internet connection more than ever. However, your Wi-Fi router often comes with less-than-ideal default settings, in some cases making the home network vulnerable to security holes and opening up the entire network to exploitation. While there are many things you can do to better protect your home network, we’re going to focus on some common fundamentals:
- Setting a strong network password and security method
- Install router updates
- Conduct a device audit
- Use a guest network for risky devices
- Turn off risky bells and whistles
In this guide we are going to talk about the basics of securing your home router. This process may look slightly different for you, but most or all of these options will be available on your router.
Log into your home router

Chances are your router has a sticker on it, listing Wi-Fi network name (or SSID) and password for the wireless network. Unless you or someone with access to your router changed the SSID and/or password, you can simply use this information to connect to it. In the same way you would any other Wi-Fi access point, try joining the wireless network.
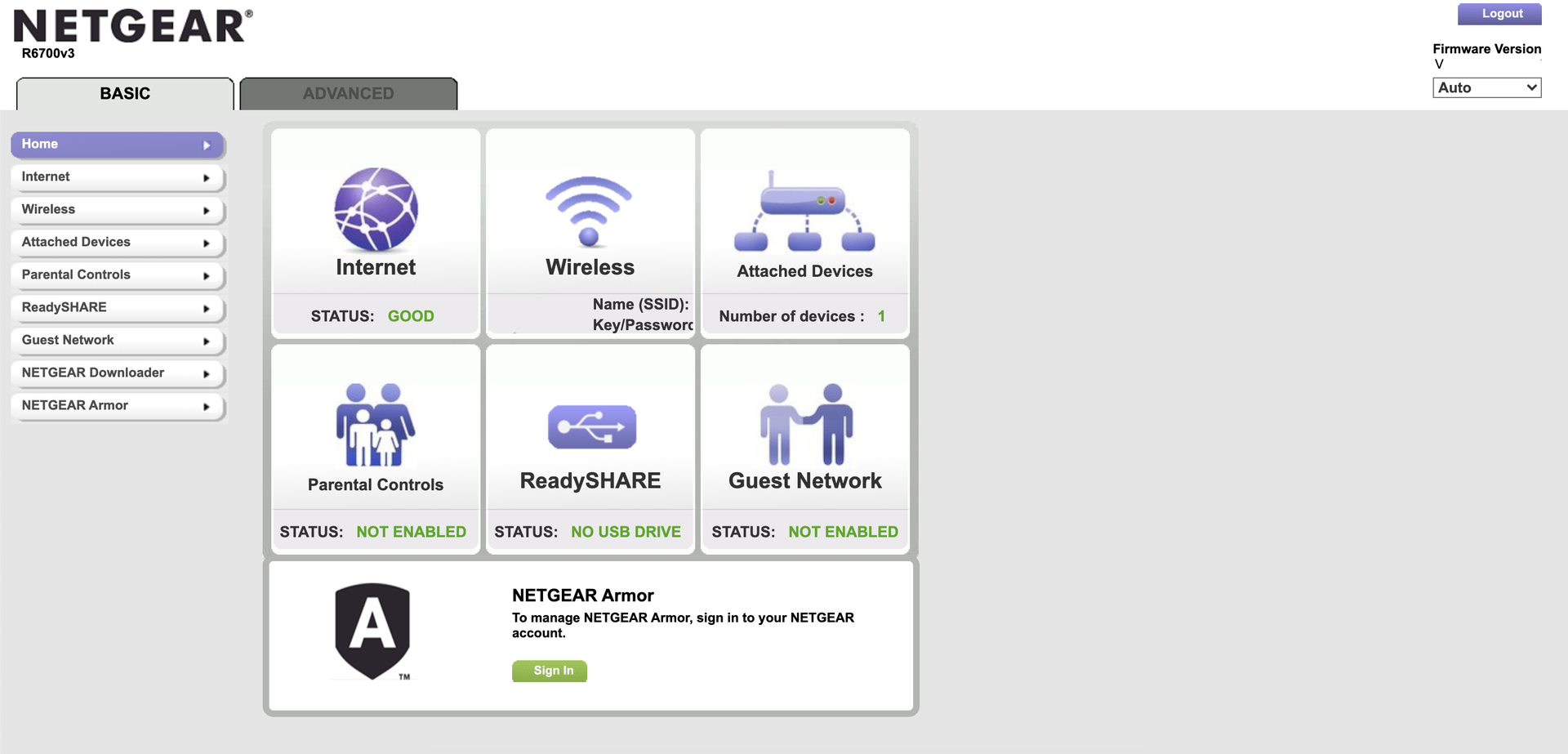
Once you are connected to the wireless network, you can also log into the router itself, which will typically have a web interface that you can visit just like any website. The same sticker with the Wi-Fi password may also have information about how to log into the router from a web browser on one of your devices (e.g., routerlogin.net; 192.168.0.1; 192.168.1.1) accompanied by a username and password. Type this website or IP address into your browser. If all goes well, this will open the router’s interface, where you will be asked to log in. (Unless you’ve changed it previously, you can use the username and password listed on the sticker.)
Configure a secure network password and security method
Because each router may have a somewhat different menu, you may need to click around your menu to find some of these options, but there’s a good chance most or all of these settings are available to you.
Use a strong security method

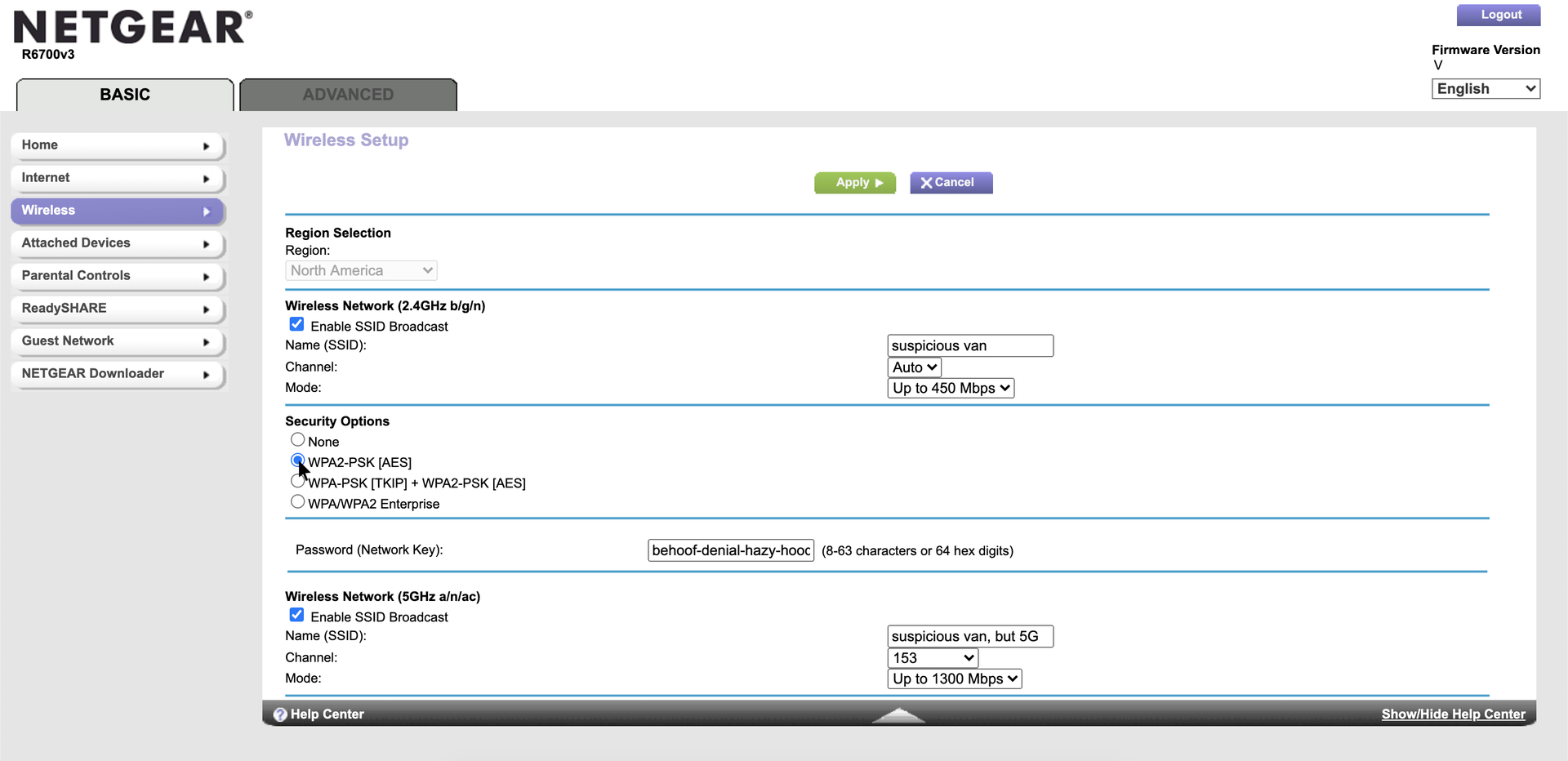
You may have several connection security methods available, including WEP, and multiple versions of WPA or WPA2. Right now, a new security method called WPA3 is slowly being added to some new routers and devices. For most modern devices, you’ll want to choose WPA2 (AES). Some devices only support WPA2 (TKIP). If WPA2 (AES) is not available, use this instead. Likewise, older routers may lack the option for WPA2, so if it’s not available, choose WPA instead.
Next, we will need to set a strong password.
Setting a strong password
Much like your device can pick up wireless signals to see the name of anyone’s nearby routers, it’s also possible to intercept the encrypted traffic that your computer and router broadcast through the air. In turn, if your Wi-Fi password is weak, this captured wireless data can also be used to discover the Wi-Fi password, allowing hackers to break into your network. Hackers typically will automatically cycle through thousands, or even millions of common passwords in a matter of seconds based on publicly available password lists. You can make their job harder by using a password that is hard to predict.
To find the characteristics of weak passwords, we can look to research into previous large-scale password breaches. Unfortunately, we know people frequently use short passwords (e.g., 123456), with common patterns (e.g., letters only, or ending with digits). We also know it’s uncommon to use symbols (e.g., the plus or minus symbol).
Instead, strong passwords are so random that they are challenging to predict. We generally expect passwords to be stronger when…
- They are long. The longer, the more difficult they are to crack.
- They lack clear patterns.
- They take advantage of symbols.
- They are unique. Using the same password in many places means one password breach could make you less secure on multiple services.
We wrote about many ways to create a strong password. A truly random set of characters (e.g., “CfdkxPc!izFC-sng9k*c”) may be difficult to type in on mobile devices, so instead, a randomized passphrase (e.g., “behoof-denial-hazy-hoodwinked!”) may be a good starting point. In the example here, we have used truly random words to create a password that’s easy to type, but still long, unique, and includes symbols.
Install router updates
We know that some malware is designed to leverage router access to data from other devices on the network. Just like your phone or computer, the router needs occasional updates to protect against vulnerabilities that target your router model. Unfortunately these vulnerabilities are fairly widespread, and can give hackers a dangerous foothold.
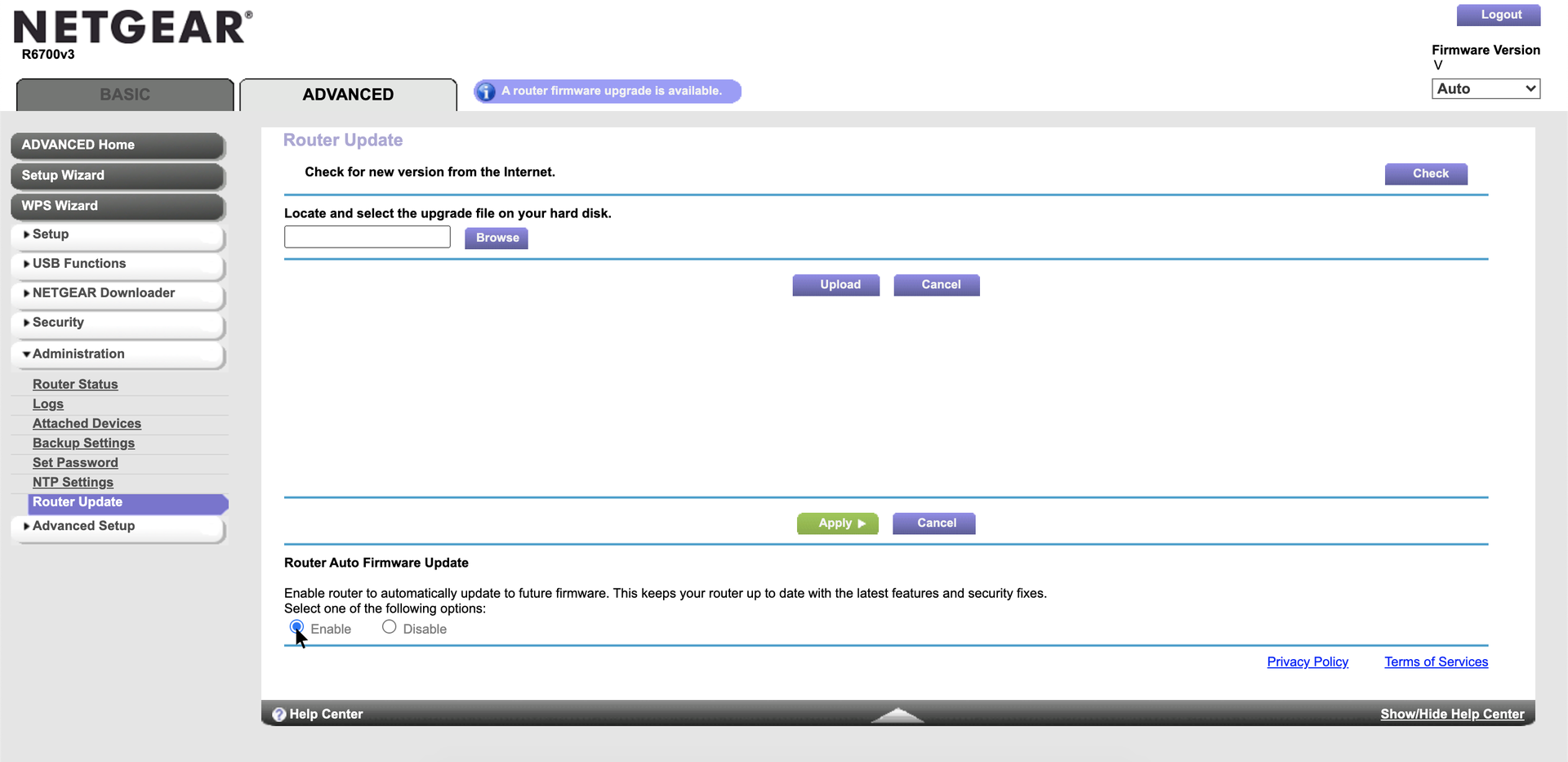
In our example, this router provides a handy notification that there are firmware updates available. But your router may be different, and you may need to look around (e.g., under Advanced Settings) to find the page to install your router updates.
If you see an option to automatically install updates, be sure to enable it to get updates installed as soon as they’re available.
If your router no longer has the option to receive a firmware update, it might be time to purchase a new one, or rent a newer one from your internet service provider.
Conduct a device audit
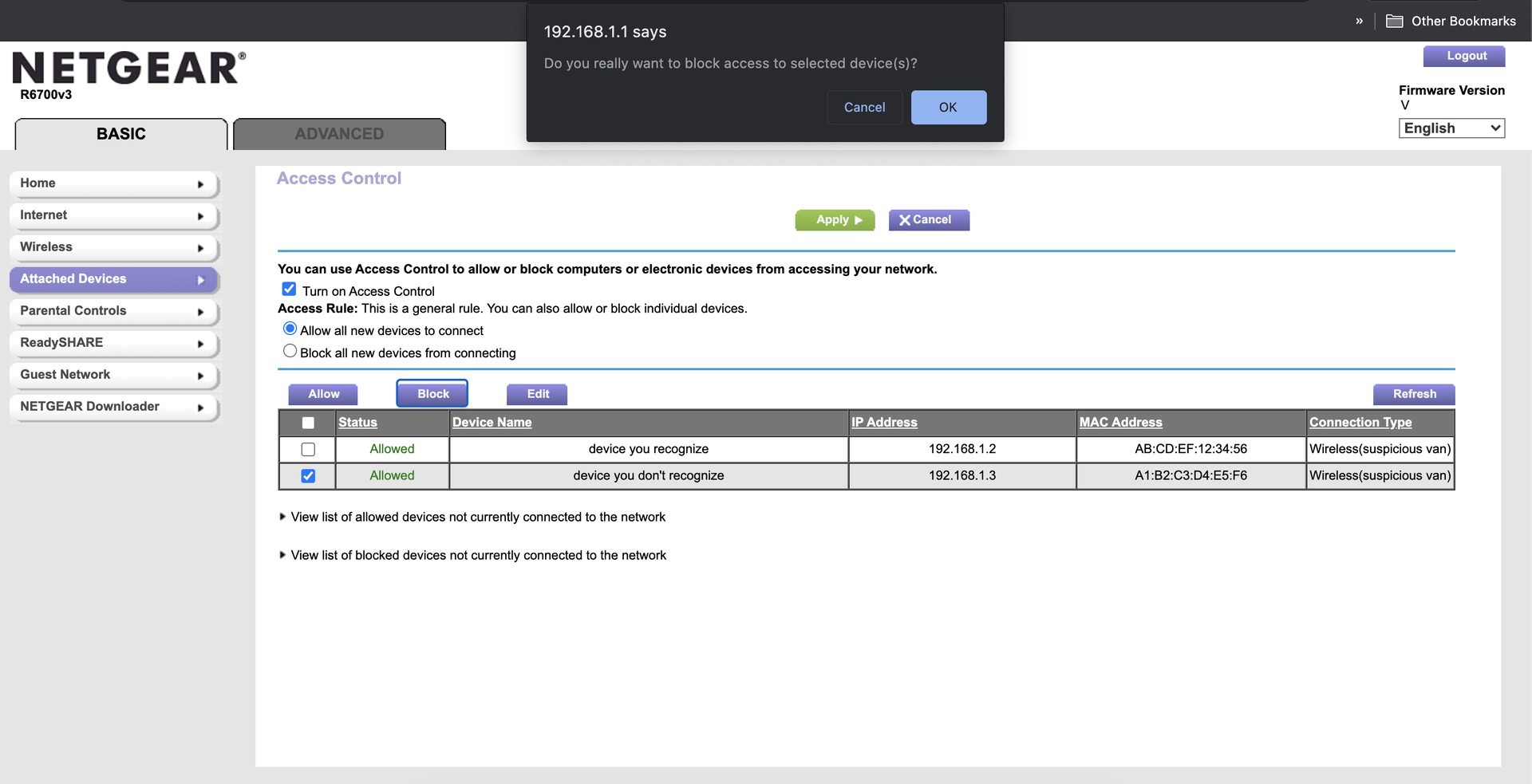
You can conduct a device audit by identifying every device on the network, and seeing if there are any you don’t recognize.
If you have a lot of devices, write down your permitted devices to ensure there are no surprising devices on your network. (After you have enough devices on the network you will inevitably forget which are which, so take notes!)
First, devices on the network will have a device name (e.g., “My iPhone”) and a MAC address (e.g., AB:CD:EF:12:34:56), an identification code meant to differentiate devices on the network. When connected to the network, many of your devices will allow you to uniquely identify them on the network by opening the device’s settings, and finding the device MAC address (e.g., under “About this device”). By comparing the MAC address on your device to the list of devices on the router, you can identify this device in the list. Continue identifying as many devices as you can.
Some connected devices (e.g., older printers) may not have a simple way to check the MAC address directly from the device, but you can still check to see if they are under your control.
First, start with a single device in your list of network connections. Find the device, and turn off its Wi-Fi connection. (This can’t be the current computer you’re using to connect to the router.) Check your router’s device status page to see which device is no longer connected. If all goes well, you’ve identified this disconnected device on the network, and it can be safely reconnected.
Try to identify all devices on your network by repeating this process with other devices, one-by-one. If you see any devices you can’t account for, it’s possible someone in your home has set up a connection you’re not aware of, or it’s a device you forgot about. But in some unusual circumstances, this could mean someone is accessing your network without permission.
Optionally, to block network connections, locate your access control menu. You can select unwanted devices, and block them on the network. If you see any unwanted devices on your network, it might also be a good time to change your network password.
Use a guest network for risky devices
Some connected “Internet of Things” devices (e.g., your Amazon Alexa) have a well-resourced security team to push out security updates, but many more devices (e.g., off-brand internet-connected light bulbs) will never receive critical security updates that could protect them from remote hijacking. No joke — hackers love internet-connected light bulbs.
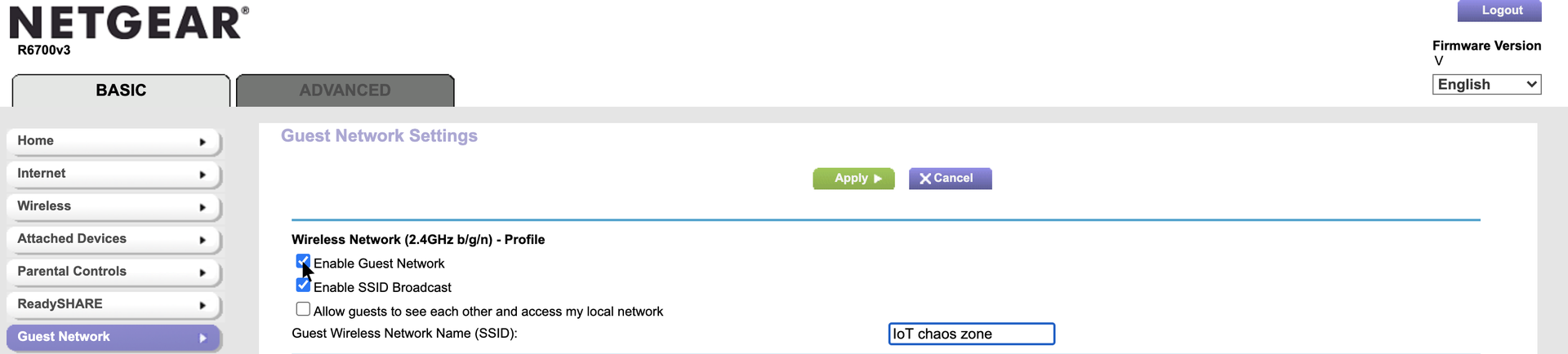
The safest thing to do is to avoid using internet-connected devices unless you’re confident they are receiving updates. But the truth is, sometimes it’s tough to stop using these devices (e.g., if you have a connected television). To isolate these devices from the rest of your network, consider placing them on a guest Wi-Fi network. When isolated on the guest network, you can be more certain that if an unpatched device is hijacked, the breach won’t affect the rest of your devices. Find your guest menu, and be sure to use a strong password, just as with your primary network.
Note that some devices (e.g., Google Chromecast) may work best when on the same network as the rest of your devices, so think through which devices are most appropriate to place on the guest network.
Turn off risky bells and whistles
There may be a few features you don’t use on your home network that introduce needless risk.
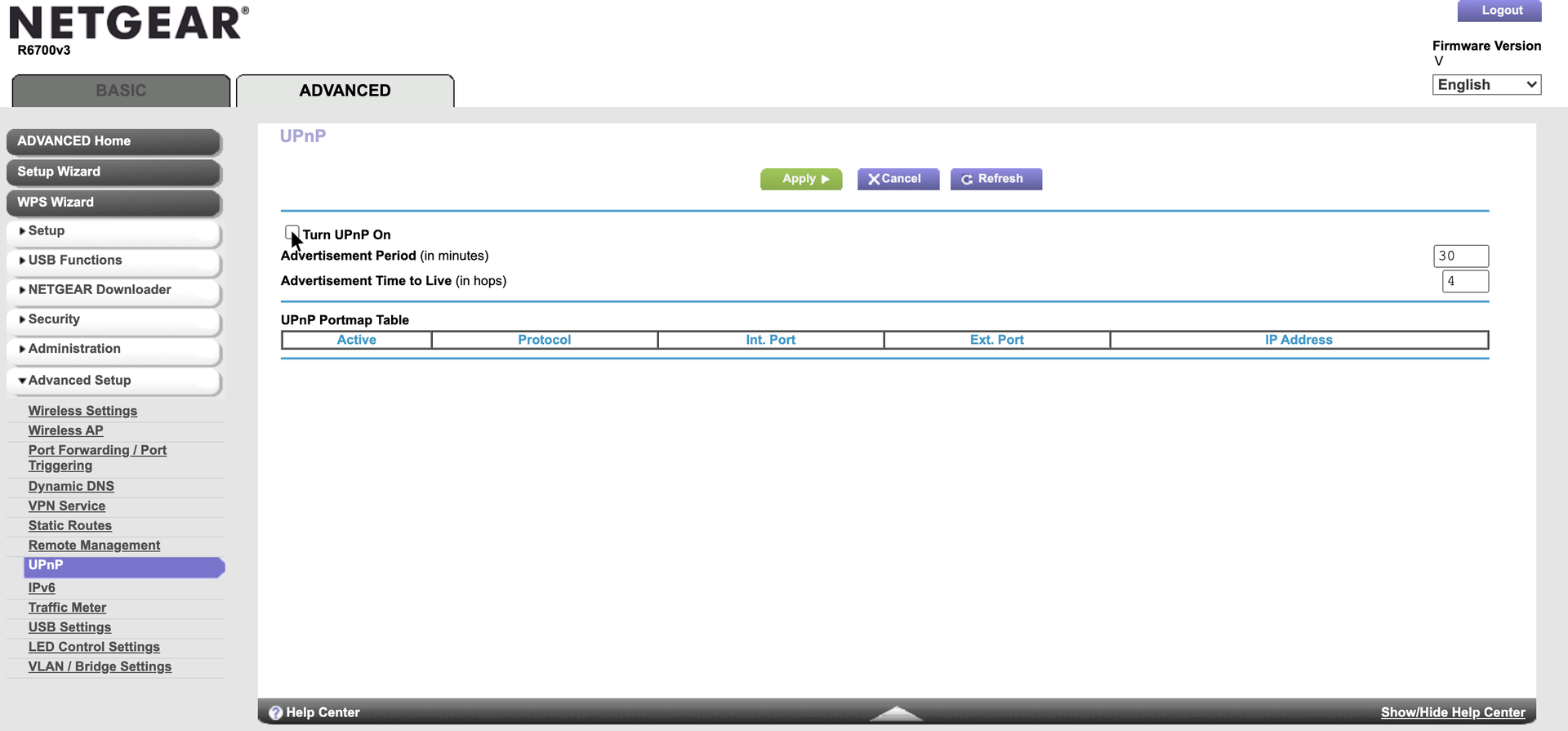
Unless you really need them, here are a few things to consider turning off.
- Turn off Universal Plug and Play (UPnP). UPnP helps devices discover one another on the network, and connect to the internet. The problem is that it also contains a number of vulnerabilities that make UPnP-enabled devices accessible to remote hackers, and many supportive devices will never receive security updates. It’s safest just to turn it off.
- Turn off Wi-Fi Protected Setup (WPS). WPS is designed to help devices connect to the network more easily through a simple 8-digit code. But once again, it also has significant vulnerabilities that make it easier for hackers to iterate through guesses, steal the code, and then connect to the network.
- Turn off remote management. This is just what it sounds like: It allows you to log into your router by navigating to it over the web. It also conveniently allows anyone to navigate to your router. Once broadcasting to the web, the router may be revealed to internet scanning services (e.g., shodan.io), opening the router to attack from anywhere in the world. Chances are remote management is already turned off, but because it’s so dangerous and you probably don’t need it, we strongly recommend confirming it’s disabled.
Reach out!
Congratulations on your tightly configured Wi-Fi router! We also have several more tips for journalists to upgrade their security while working from home. Freedom of the Press Foundation provides personal assistance to journalists on digital security threats and concerns. Reach out at freedom.press/contact. Happy surfing.




