
When working together online, chat tools like Slack are useful, but allow the service provider to read your messages. Keybase simplifies the process of sharing files and having conversations securely.
Keybase is end-to-end encrypted, meaning that only you and your conversational partners can read the messages and files you send over the app. The Keybase application is also open source, meaning that its code is publicly viewable. After responding to a (2019) security audit, the team has created a strong, but fairly easy-to-use collaboration tool.
There is some history to consider. In mid-2020, Keybase was acquired by Zoom, which has had its fair share of security controversies, leading some Keybase users to demand the company make more of its code publicly available. At the same time, the Keybase team’s experience helped Zoom quickly roll out end-to-end encryption, allowing its millions of users the option to securely chat over video.
The beauty of Keybase, however, is that you don’t really need to know much about security to use it. This guide will help you get started setting up and using Keybase. While Keybase does support features for more technical users (e.g., using external encryption keys), for our purposes, we’ll stick with the basics. For those looking for more advanced features, check out Keybase Book.
Getting started with Keybase
First thing’s first: Go to Keybase.io and click the “Install” button at the top of the screen, or find it for your mobile device in the iPhone App Store, or Google Play store on Android.
Download Keybase for your preferred desktop computer or mobile device, and follow the installation instructions.
Once it’s installed, open Keybase and select “Create an account” and choose your username. Your username cannot be changed, so pick a good one!
Next, choose a name for this particular device. It’s important to note that this device name will be attached to your profile, and will be publicly visible from the Keybase website.
You can optionally add a phone number and email address. This is up to you, but keep in mind that if you do submit this contact information, anyone with your phone number or email address will be able to find you more easily within Keybase.
Finally, click “Finish” to start chatting.
Start a conversation
From the Chat tab, you can start new conversations with other Keybase users. Click “New chat” to search for a friend using their Keybase username. When you’ve found your partner, click “Start” and get to chatting.
Making a team
From the “Teams” tab on the left, you can similarly make a group chat for friends, or for an organization. (You can optionally add more channels to a Team chat later.)
When inviting someone to a team, you can give them four different types of team members, depending on how much control over the group you’d like to give them:
- Readers: Readers can write in the chat and read (but not submit) files to a team folder.
- Writers: Writers can create chat channels, as well as read and write in team folders.
- Admins: Admins can do anything a Writer can do, plus add and remove members, and change team members’ roles.
- Owner: Owners can do anything an Admin can do, and they can also delete the team.
When setting up Teams, Keybase may also ask for access to your system to allow you to share and receive files with team members.
Automatically delete messages
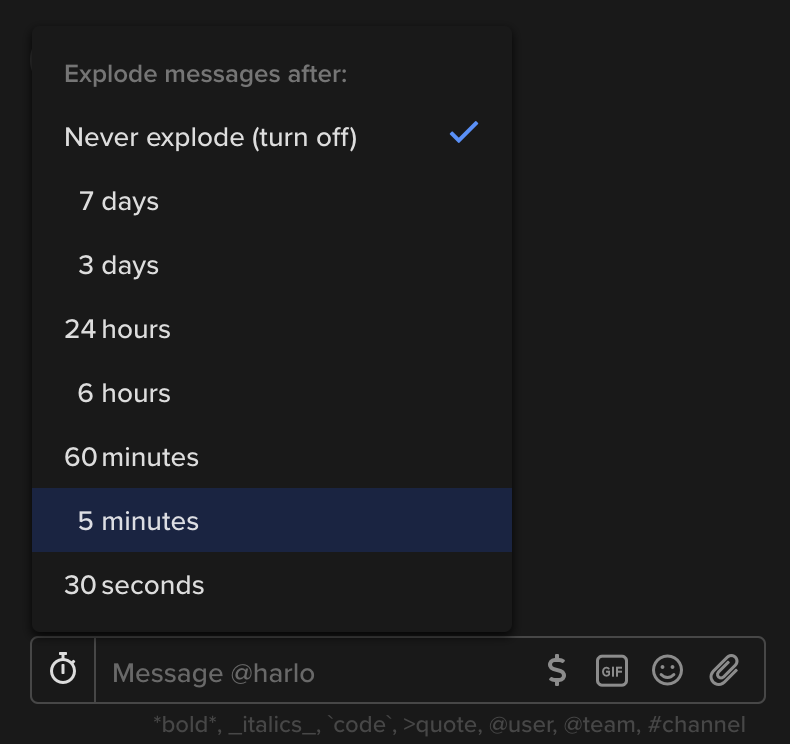
Most messengers will keep your messages until your account is deleted, or until you manually delete them. With Keybase, you can set messages to automatically delete after a duration you choose. Within any conversation, click the timer icon at the bottom of the screen. You can set messages to “explode” in that conversation between 30 seconds to seven days of being sent.
Storing and sharing files
You can also share files or upload them for safekeeping from the Files tab.
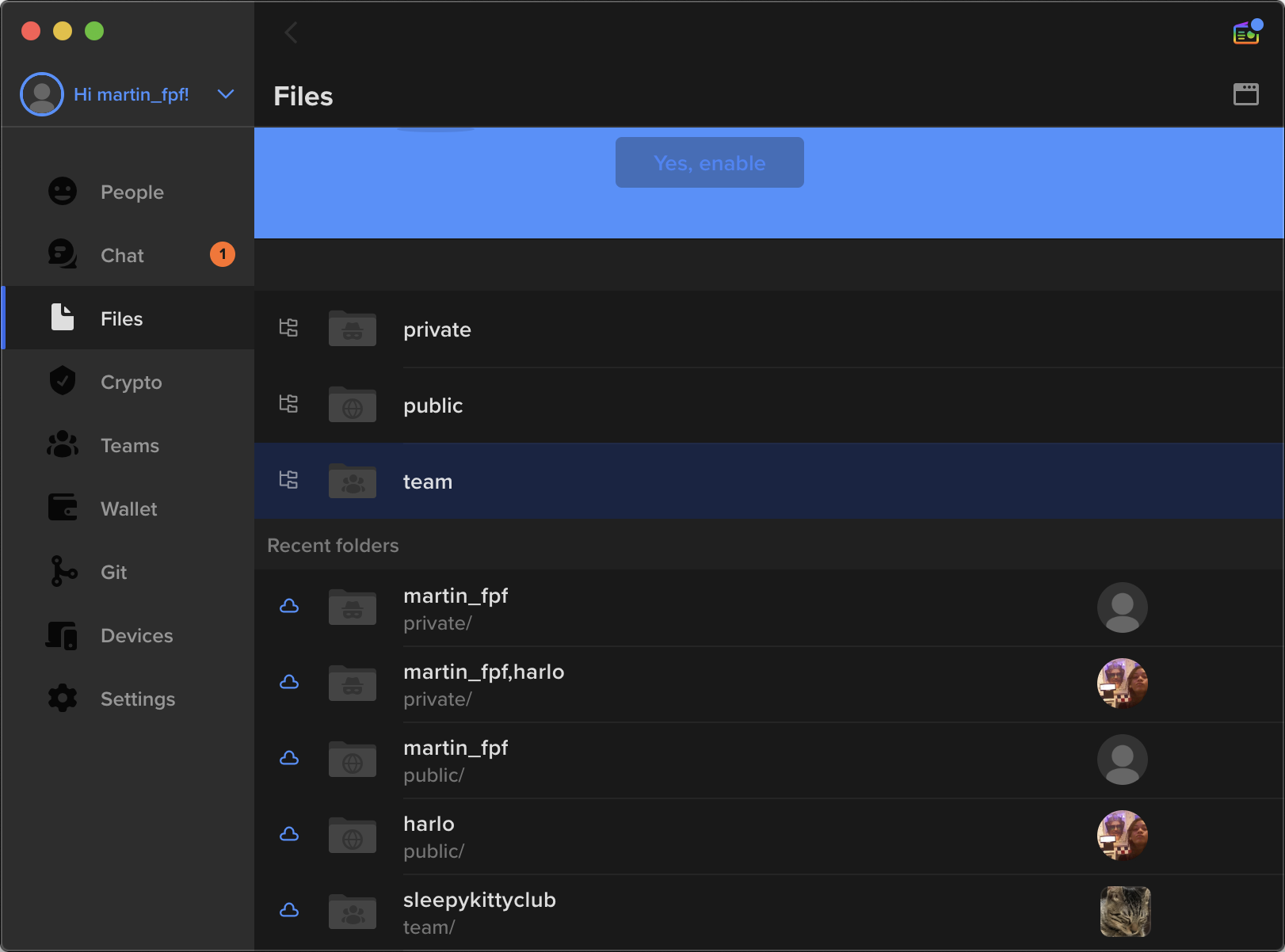
You can keep your files in three types of folders, depending on how you want to share them.
- Private folders: For files that can only be read by you, and anyone you choose.
- Public folders: For files you’d like to make accessible to anyone on the internet.
- Team folders: For files that can only be accessed by one of your teams.
To upload files for certain people, use the private folder. For example, when you want to upload a file for your own safekeeping, you can click on your private folder, and click on your own username to upload anything you’d like for yourself. From the private folder, you can also click on a folder with a contact’s name to share files with them. From team folders, you can similarly share files with any team you have joined.
Finally, you can sync files on your device, allowing Keybase to automatically download the most recent version of the folder and its files. To enable this, hit the “Sync to this device” switch at the top right of any file folder.
Note that if you’re going to sync files to your device, it’s really important to trust people on your team, because they can upload files that may automatically appear on your device. If you don’t trust them, avoid opening their files or disable sync.
Attaching identities
When searching for another person on most chat platforms (e.g., Twitter, Instagram), you might use their photo and name to identify them. However, it’s tough to say for certain that you’ve found the right person. Sometimes people don’t use a familiar username or photo; in some cases, you might even find impersonators.
Keybase helps solve this problem with proofs — methods to prove you own other accounts your friends may be familiar with, such as your Twitter account. You can prove you own an account by posting something there, generated by Keybase.
For example, you can prove you own a Twitter account by posting a tweet with very particular text.
Click your username at the top left corner, and click “View profile.” From here, you click “Prove your Twitter.” Type in your username. You should see the text they want you to post.
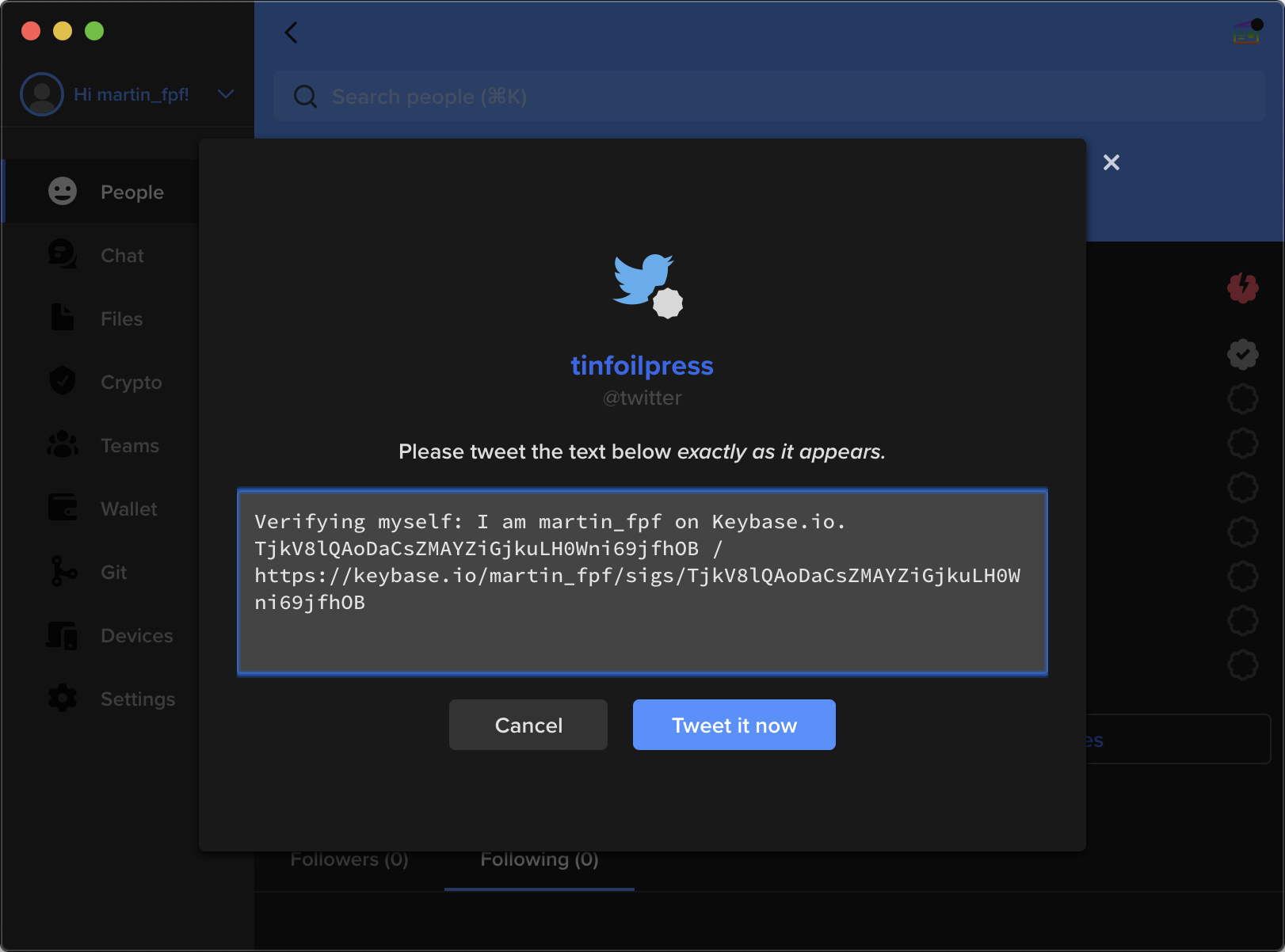
Click “Tweet it now” or copy this text and tweet from your Twitter account.
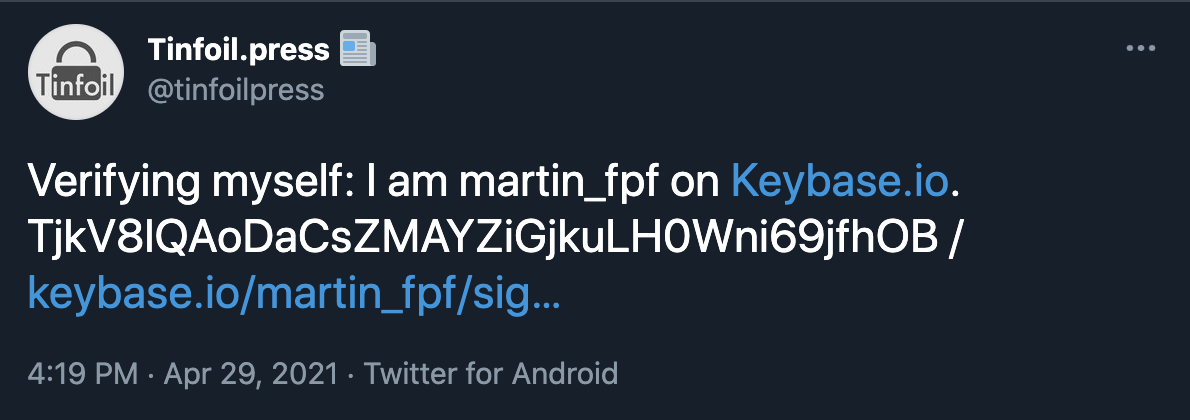
Next, “OK tweeted! Check for it!” to complete your proof. Your Keybase profile will now display your Twitter profile.
You can repeat this step for other identities you’d like to attach to your Keybase profile. Just remember: because proofs are intended to help people find you, they are entirely publicly visible.
Make a backup
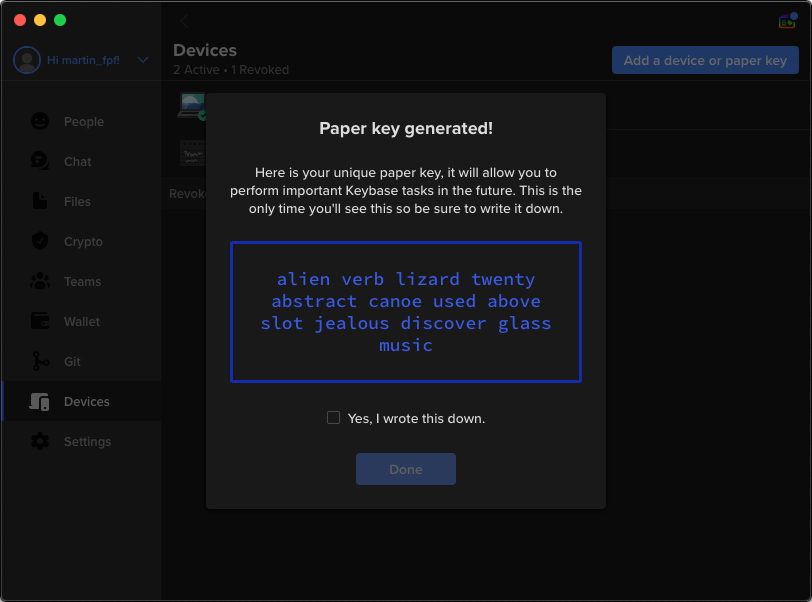
Because Keybase is end-to-end encrypted, only your devices can unscramble the messages. In case you ever lose access to your devices, you’ll want a backup plan. To maintain access to Keybase, you’ll need an emergency passcode, which Keybase calls a “paper key” — essentially it’s a randomized key to unlock your account. Generate your paper key:
Devices > Add a device or paper key > Create a paper key
You can also add other devices from here, such as a mobile device. Keep a copy of your paper key somewhere safe, like a piece of paper or external drive in a trusted location, or a password manager.
Keybase is not bulletproof
While Keybase is a powerful suite of tools, you should also take care to use it safely.
First, by default Keybase allows anyone to contact you. If you are concerned about receiving messages from unwanted contacts, consider changing this in your settings:
Settings > Only let someone message you or add you to a team if… > You follow them
Likewise, if you have configured Keybase to allow for people to share files with you, be careful that you really trust the people sharing these files, particularly if you have configured Keybase to allow direct editing of files on your devices (e.g., by using FUSE on Mac). This is another reason that proofs are valuable; this makes it fairly easy to check that you are sharing and receiving files with the right people.
Last, know that the names of devices you attach to your Keybase are publicly available (e.g., martin_fpf’s devices). If this is a privacy concern, be mindful of the names of devices you add to your account, consider giving new devices generic-sounding names that would not be too meaningful.
You’re caught up!
That’s what you need to know to get started with Keybase. If you want to learn more about advanced features within Keybase, check out this Keybase Book for additional details. Read more from our digital security team about tools and practices that will help you communicate securely.



