
Photo by Bill Couch. CC BY-NC-ND 2.0
Once upon a time, Microsoft Office provided a small suite of applications on your computer, including Word for writing, Excel for spreadsheets, and PowerPoint for presentations. But increasingly, modern newsrooms use Office 365 to access these tools over the web, alongside remote storage and team management software. While working on the web offers obvious advantages, many reporters also wonder about the privacy and security of this data. What about our most sensitive, unpublished details when reporting? What can Microsoft see?
There are dozens of tightly integrated apps available under the umbrella of Office 365. To name just a few, beside the traditional desktop applications we’ve got…
- OneDrive (file hosting and collaboration services)
- Outlook (hosted email services)
- Azure Active Directory (identity services)
- SharePoint (web application and collaboration platform)
- Microsoft Teams (video, audio, text chat services)
- Yammer (social networking services)
When hosted in Microsoft’s servers, the company has everything they need to read your data, by default. And like many U.S. tech firms, U.S. agencies may compel Microsoft to provide relevant user data to aid in investigations. Office 365 also provides tools for workplaces to monitor and retain records of employees’ activities. The good news: Microsoft provides several ways to prevent the company from reading your data.
Compared to Google Workspace, Office 365 offers a much more flexible series of options for storing data, allowing organizations to host some data on their own servers, Microsoft’s servers, or a combination of both. They also offer some strong controls to Enterprise customers that wish to constrain who can look at their data. In limited ways, users can even prevent Microsoft from seeing their data.
Office 365 is powerful and adaptable, but journalists should nonetheless understand what is visible, and to whom. For most organizations a great deal of data is available to Microsoft, but because every organization can configure how it will handle user data quite differently, it’s worthwhile to learn how your organization secures your data on Microsoft’s services.
What can Microsoft see?

Microsoft's Quincy, Washington data center. Source: Richard Duvall
In Office 365, Microsoft works in the background to scan for suspicious emails and files sent to your accounts. The service flags suspicious activities to administrators, and proactively defends against the attacks it identifies among other organizations using Microsoft’s services. But to provide these capabilities, Microsoft needs remarkable visibility into subscribing organizations’ accounts.
When connecting to Office 365, the connection is protected by strong encryption, scrambling and making it unreadable to eavesdroppers as the data moves through the web, to and from Microsoft. Similarly, data at rest on Microsoft’s data centers, where Office 365 data is housed in an encrypted format so that it can’t be read unless someone with the necessary access needs to unscramble it.
Still, there are many reasons Microsoft may end up reading your data.
Microsoft says in their security documentation that they do not use Office 365 data for advertising purposes. Instead, they leverage user data for several purposes, including giving the company access to troubleshooting services, and to scan for spam and malware. Microsoft also says they reserve the right to review the content of users’ accounts to enforce the terms of its service agreement.
Microsoft pulls in user data from many of its services to identify unusual activities within an organization, and patterns in attacks across organizations using its services. This includes your organization and other organizations. Subscribers share some data with Microsoft, including indicators of spam, as well as malicious files and websites received in emails. In turn, its threat protection services learn from these attacks and proactively identify them to other organizations and services.
While Microsoft offers cheaper Business subscriptions with fewer features, additional security features are available to larger organizations with an Enterprise subscription. In general, the highest Enterprise tier, which Microsoft calls E5, offers the most robust tools to administrators for monitoring security incidents, followed by E3.
For Enterprise customers, Microsoft’s Advanced Threat Protection is designed to scan for threats within its services (e.g., email with Microsoft Exchange Server, or remotely with Exchange Online). Your organization’s administrators security tools can be monitored through Microsoft’s Security and Compliance Center.
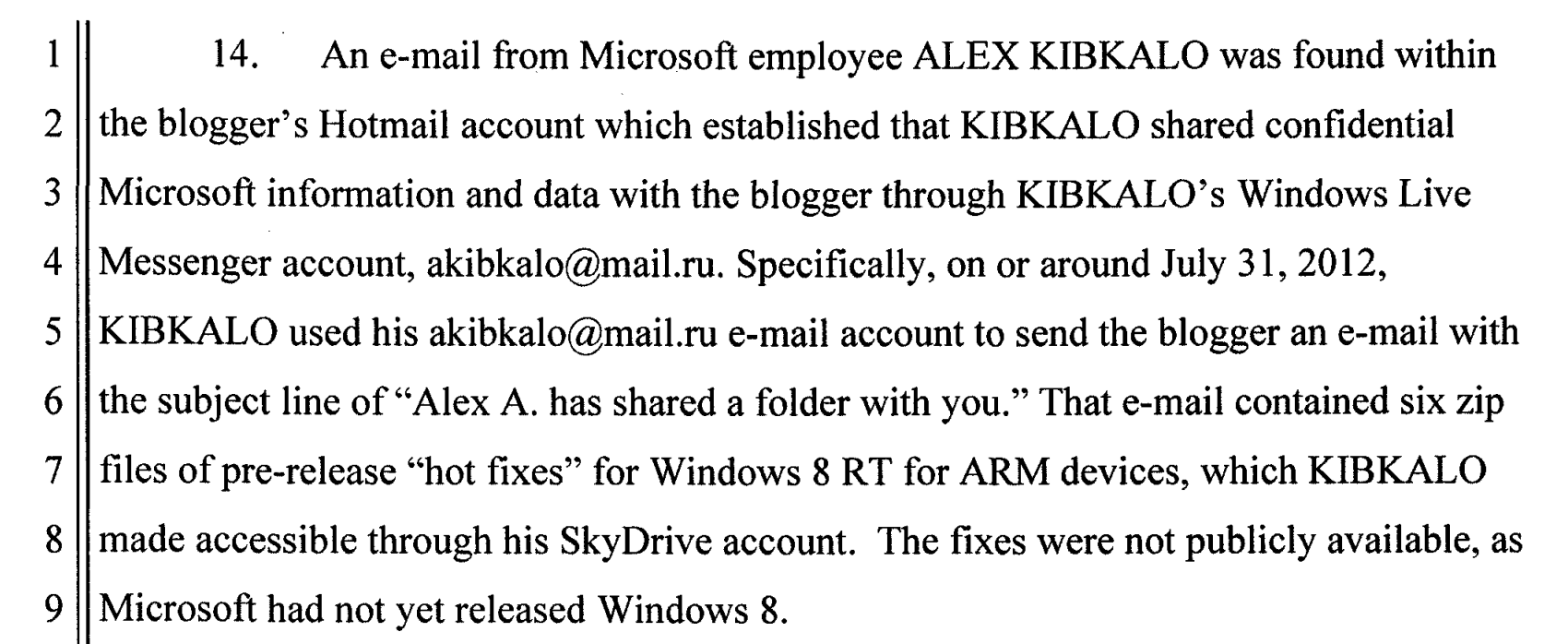
Sidebar: We know of at least one case where Microsoft has used its capability to read journalistic data. In what they’ve called, “exceptional circumstances,” as part of a leak investigation into an ex-employee who shared unreleased software with a blogger, Microsoft used their unique access to user data to mine the blogger’s personal email account. (This did not appear to be an Office 365 account.) Microsoft says they have since heightened the demands of their review process to include outside legal counsel, rather than making these decisions entirely on their own.
Enterprise users can prevent Microsoft from accessing their data
While Microsoft touts the security advantages of using their cloud, as opposed to hosting data on your own servers, they also support options for organizations that prefer to keep data in-house, as well as tools for giving Microsoft selective access to user data.
The highest-tier Enterprise edition offers the greatest capabilities to constrain Microsoft’s access to user data — typically called the Enterprise “E5” edition.
For example, the Customer Lockbox allows organizations to require permission before a Microsoft employee can access their data. This ability is only available in the E5 version, or with a paid add-on for other Enterprise plans. As Microsoft says in their documentation…
"Occasionally, Microsoft engineers help troubleshoot and fix issues that arise with the service. Usually, engineers fix issues using extensive telemetry and debugging tools Microsoft has in place for its services. However, some cases require a Microsoft engineer to access your content to determine the root cause and fix the issue. Customer Lockbox requires the engineer to request access from you as a final step in the approval workflow. This gives you the option to approve or deny the request for your organization, and provide direct-access control to your content."
The E5 edition also offers a service called Customer Key, which allows organizations to use their own encryption keys to manage stored data for regulatory and compliance purposes.
While most of these tools apply to how administrators manage the service, one thing journalists may appreciate for day-to-day work is Office 365 Message Encryption, available to E3 and E5 users. This feature allows users to selectively send a secure email, so that only the recipient can read it. Even Microsoft can’t read these encrypted emails.
It’s possible to host some Microsoft services on-premises, meaning that your organization can manage the physical server yourselves. When you own the server, you are responsible for its security and safety, which may introduce new risks. On-premises Microsoft servers are also designed to tightly integrate with Microsoft’s remote services, so storing the server in your building doesn’t necessarily mean your data is private. But this does introduce some opportunities to control where your organization physically stores your data.
Microsoft provides options to selectively withhold your sensitive on-premises data, with Hold Your Own Key (HYOK). What does this mean? If your organization’s administrator thinks something in your Office 365 emails, documents, files, or websites should not be exposed to Microsoft, they can apply a policy to set it up that way. This is not something an ordinary journalist would do with their personal documents, but rather, controlled by your administrator. Because documents protected by HYOK are encrypted, however, they will not be easily searchable through the cloud like ordinary documents within your Office 365 domain.
Many of these security features are only available to E5 subscribers — Microsoft's most expensive tier. Unfortunatley, accessing these valuable security features may be prohibitively expensive for many news organizations, leaving data legible to Microsoft by default.
Physical protections
Microsoft says that they provide several protections at their data centers. Employees must request permission to enter the data center with appropriate business justification, and provide the appropriate keycard, as well as biometric authentication with a handprint. Employees will only have access to the relevant part of the data center. Closed-circuit television cameras inside and outside data centers, recording at all hours. The company logs and audits who comes in and out. Likewise, their servers monitor for unexpected changes in the software.
While we know a lot about the data centers themselves, we don’t have quite as much information about how these rules work in practice. We don’t know how many people at Microsoft have access to user data, what kind of data, and under what circumstances. When Microsoft is compelled to share user data for a legal request, how many people have access in practice? We don’t know.
What we can say is that Microsoft has said in their security documentation that they constrain access to “essential personnel,” log employee access to user data, and conduct both internal and external audits on employee access.
What can government agencies see?
In the United States, government agencies can compel U.S. communications providers to disclose information about their users, including Microsoft.
The most common type of request, a subpoena, may yield valuable data about the user’s account. This includes the IP address and connection history, which can be used for a rough estimation of the user’s location and patterns of movement. Microsoft calls this “non-content” data.
The content of a user’s account (e.g., the words in an email, or a document in Microsoft’s cloud) generally requires a warrant.
According to Microsoft's law enforcement requests report, in the first half of 2021, the company received 6,392 U.S. requests for 14,195 accounts, complying with roughly 88% of those requests. However, the number associated with Enterprise cloud customers is much lower.
"In the first half of 2021, Microsoft received 121 requests from law enforcement around the world for accounts associated with enterprise cloud customers. In 70 cases, these requests were rejected, withdrawn, no data, or law enforcement was successfully redirected to the customer. In 51 cases, Microsoft was compelled to provide responsive information: 31 of these cases required the disclosure of some customer content and in 20 of the cases we were compelled to disclose non-content information only. Of the 31 instances that required disclosure of content data, 27 of those requests were associated with US law enforcement."
When it comes to Office 365 data, the company says it “redirects government requests for your data to be made directly to you unless legally prohibited and has challenged government attempts to prohibit disclosure of such requests in court.” (Indeed, they have.)
In most cases, Microsoft says courts generally do redirect such requests to enterprise customers. What does this mean?
When Microsoft receives a request for your organization’s user data they will probably redirect the request to your organization, so at least you’ll know about it. But in an unlucky minority of cases, your organization may never be informed if they are the subject of such requests.
While there’s no shortage of cases where Microsoft has been compelled to share user data with U.S. agencies, we have not yet seen a publicly disclosed case where a media organizations’ user data has specifically been requested by, or granted to the U.S. government. Time will tell!
What can your employer see?
It’s safe to assume your administrator can see nearly anything you do in Office 365. Global administrators — basically, whoever set up your Office 365 domain — can see most activity within your Microsoft services. They can also selectively share this access, giving other users administrative powers as well.
Office 365 offers several versions for both Business and Enterprise — you can see all of the differences here and here. In both, Microsoft offers a few tiers of service, each with additional services and tools for analyzing an organization’s user data. Generally, the Enterprise editions offer customers the greatest visibility into users’ data. The highest Enterprise tier, which Microsoft calls E5, offers analytical tools and the greatest visibility into Office 365 users’ activities, followed by the E3 edition.
Office 365 Business and Enterprise versions offer audit logs, allowing administrators to monitor activities within their organization. These are records for virtually all activities in an Office 365 domain — for example, when someone logs in, opens or modifies a document, or reads an email.
Administrators can monitor user activity in OneDrive (where documents and files are stored), Outlook, SharePoint, Active Directory, and several other services. Logs may include other forms of metadata, including users’ IP addresses. Administrators can also obtain push notifications for targeted activity.
This visibility may help organizations monitor for behavior they believe is suspicious.
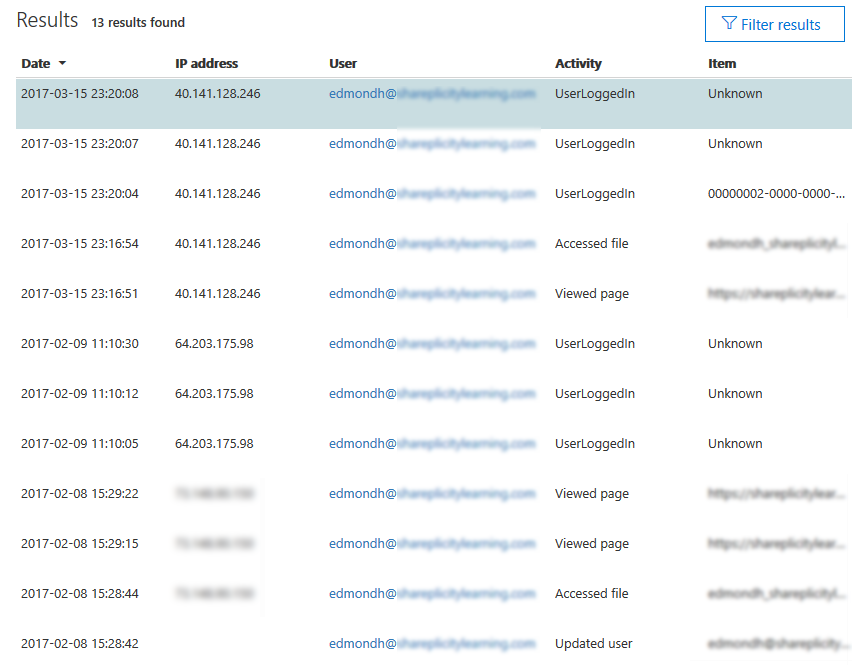
Screenshot of audit log results, including usernames, activities, timestamps, and IP addresses. Source: Nicolas Bouchard
Likewise, Microsoft offers a productivity score feature, which allows both teammates and their employers to monitor users’ activities, as well as the technology used within their team. For example, teams can see when, and how frequently people work together on documents and communicate. In turn, users’ behaviors generate a “score” that can be used to determine where changes might need to be made.
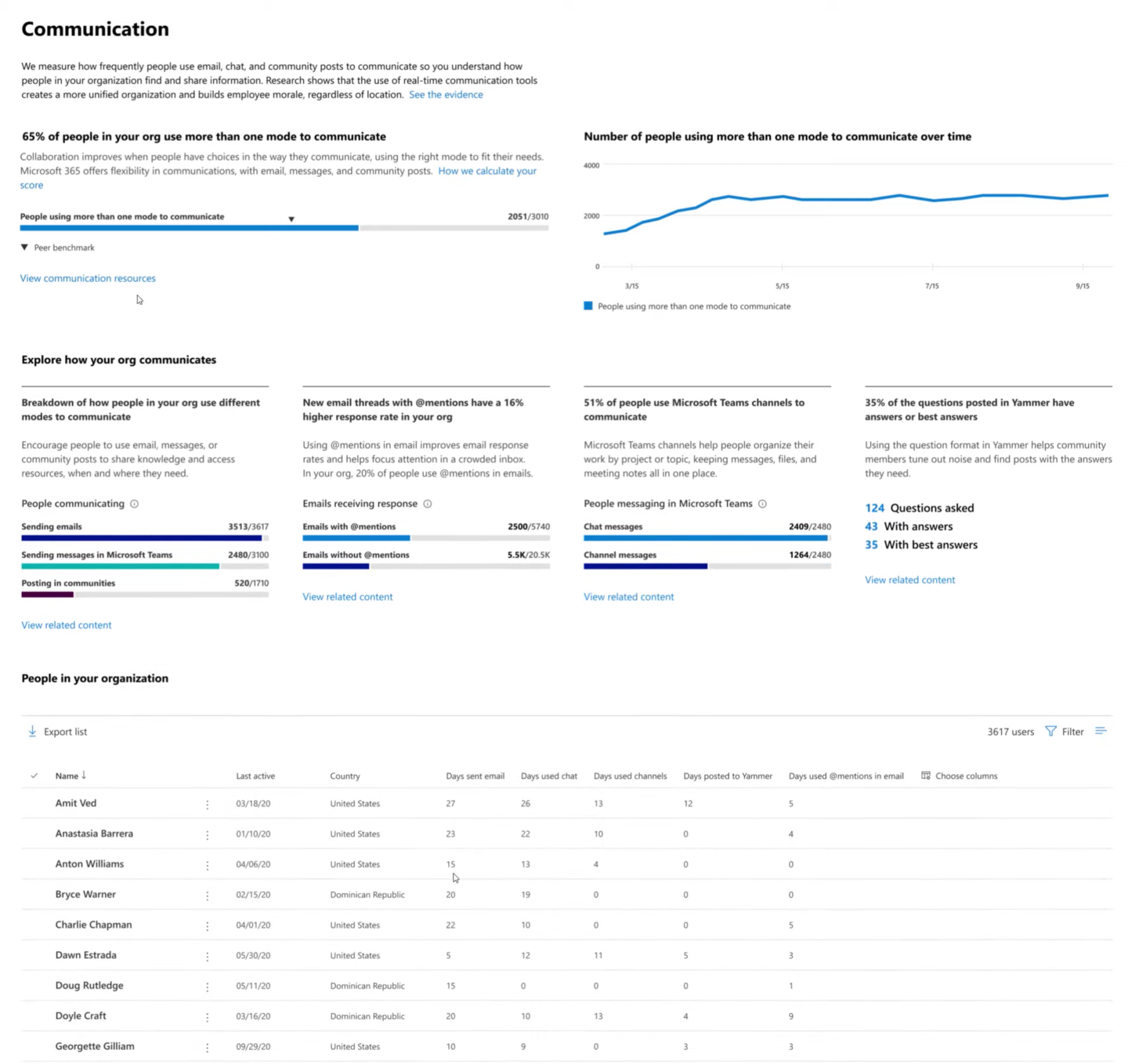
Source: Microsoft promotional video.
By default, productivity scores can drill down into the activities of individual users. Organizations using productivity scores need to opt out of displaying individual users’ activities.
For both Business and Enterprise users Office 365 also offers eDiscovery features [1], enabling organizations to search for, and create custom rules to selectively retain and analyze user data within their domain.
If you can see it, chances are the administrator can see it. They may also maintain that records of what you looked at, and when.
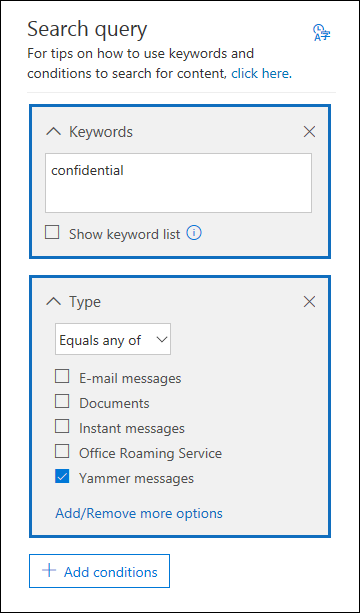
For example, when you delete an email, it’s not necessarily gone; the administrator can decide whether to retain it, or place a retention policy on the user’s entire mailbox.
While this may sound pretty intrusive, there are some legitimate reasons for administrators to be able to gather and retain this user data, such as compliance with legal requests. Logging and retention features may also be helpful when monitoring or responding to serious security incidents that may affect your workplace. Still, as someone who may work within these systems, it’s important to know that virtually anything you do in Office 365 is likely visible to your organization’s administrator, and whoever they answer to.
Using Office 365 mindfully
You still need to get your work done, and Office 365 may play a critical role. Take a couple of steps to learn how to use it in a way that makes you feel comfortable.
Consider giving yourself an Office 365 audit. Look through your Outlook, OneDrive, and potentially Microsoft-connected activity on mobile devices. If you can see it, the administrator can likely see it. Depending on how your organization configured Office 365, it’s possible that Microsoft can see it. If Microsoft can see it, it’s likely subject to requests from government agencies.
A lot of journalistic work done in Office 365 ends up in publication, and isn’t terribly secretive. However, there are some things you probably wouldn’t want to hear read aloud in federal court, such as unpublished details on your sources.
Consider getting details from your Office 365 administrator. You can delete unwanted data, but depending on your organization’s retention settings, it’s not necessarily gone. Consider doing some homework to identify your Office 365 administrators and find out what Office 365 version you have. If your organization has an Office 365 Enterprise subscription, find out what rules your organization has set up in eDiscovery, audit logs, as well as any internal policies your organization may have for administrative data retention and access. Does your organization have any policies for withholding access to Microsoft? How about other cloud providers?
Consider carefully what you put in Office 365. There are times when it’s best to store our data somewhere besides the standard configuration of Office 365. Data about internal credentials, sources, long-term investigations, and other sensitive data may belong somewhere else.
It may be that another cloud service provider that stores your data in an end-to-end encrypted format by default (e.g., Tresorit) is a more conservative choice for our most sensitive data. The main trade-off is that these services are not free. Likewise, sometimes it’s best to keep data offline or off a computer entirely.
Office 365 offers powerful tools that help us collaborate and build long-term memory in our work. But depending on how it’s configured, it may remember more than you’d like. Be mindful about how you and your organization choose to use it.
[1] There are some differences between audit logging retention and rulemaking capabilities for Microsoft's Business and Enterprise E3 and E5 editions. While Business and Enterprise versions each offer basic eDiscovery features, to export or use eDiscovery holds requires Enterprise E3 or E5. The E5 edition also includes “Advanced eDiscovery” with additional analytical tools to help users more easily identify and manage targeted user data.




