They are tethered to wireless networks, and we are tethered to them. We spend so much time with smartphones, yet most of us devote little of it contemplating our small computers. We often treat these valuable devices more like everyday household items, as opposed to curated archives of our lives.
If there’s one item in your possession housing the most information about you, it’s probably your phone. Keeping your information safe depends on learning a little more about how to choose your small computer and care for it long term.
One-time upgrades
Shopping for phones
When shopping for a mobile device, you’re often thinking about how long the phone will last. You want a strong battery, fast hardware, and lots of storage to house your apps, photos, and other data. But there’s another thing you should consider when choosing a phone: How long will the phone receive security updates?
Security updates are the primary defense against malicious code taking advantage of vulnerabilities in your devices, yet phone manufacturers tend to have inconsistent track records supporting those updates. Mobile equipment manufacturers like Apple, Google, and Samsung all have different commitments to keeping your device safe with such updates.
For example, Apple has offered exemplary support, sending critical updates to iPhones manufactured as far back as five years. Google has required many makers of Android devices (e.g., “Android One” phones) to provide security updates for at least three years.
Note this does not mean you’re getting three years of updates from your purchase date; you’re getting three years of updates from the market release of the device. For example, if your Android device was released in stores in 2022, it will stop receiving updates in 2025. However, there are some exceptions, such as flagship phones from manufacturers like Google (e.g., the Pixel series) and Samsung, which guarantee more years of security updates.
The short version: iPhones are more likely to be a safe and reliable bet, yet they’re usually much more expensive than most Android devices. If you’re going to get an Android device and you plan on using it for more than a couple of years, consider quickly searching for the model of phone you’re most excited about and see how long it will receive updates. Chances are, flagship devices such as the most recent device in the Google Pixel or Samsung Galaxy series will offer the most reliable updates. Likewise, for budget devices, consider newly released Android One devices (e.g., Motorola One or Nokia), which have promised no less than two years of updates from the release date.
Disk encryption
If your device leaves your possession, the data can be read or copied. Fortunately, it’s easy to protect the data on your disk, so that it’s only readable after you enter your password.
If you have a password-protected iPhone, your disk is already encrypted. Simply locking your phone will encrypt the device.
For Android users, it’s easy to encrypt your mobile device. Some Android devices, such as those in the Pixel line, are encrypted by default. Note that disk encryption is activated after powering off the phone. This means that solely putting the phone into sleep mode won’t activate disk encryption.
Make sure you have a good password
Disk encryption can protect the data on your device, but it’s only as strong as your password.

Kanye unlocks his iPhone with “000000” in a room full of cameras.
A password like Kanye used in his very public White House visit (see video above), isn't great. But let’s dig into it: What exactly is the problem with a password like “000000”?
We know people often use short, predictable passwords. For example, 2023’s greatest hits included “111111” and “password”. What most of these passwords have in common is that they’re easy to remember, and even easier to enter in your phone. The problem is that hackers and phone thieves know this as well.
Of course it’s possible for anyone to stand over your shoulder to see what you typed in. But even if they’d never seen you type it in before, anyone with access to software tools for cracking mobile passwords (e.g., GrayKey) can unlock the phone with enough time. Cracking tools offer automated techniques for attempting a list of likely passwords. If the likely passwords don’t work, many of these tools will try out every password possible, until it exhausts its likely options. However, this will always take time — ranging from seconds to years. By using a more unpredictable password, you can force them to wait a long, long time.

A GrayKey unit, attempting passcodes on an iPhone.
While considering a password that would still work for you in day-to-day use, get creative about using a password that people and computers would both be unlikely to guess.
There are a few common strategies for making your password less predictable, but still meaningful to you in the real world.
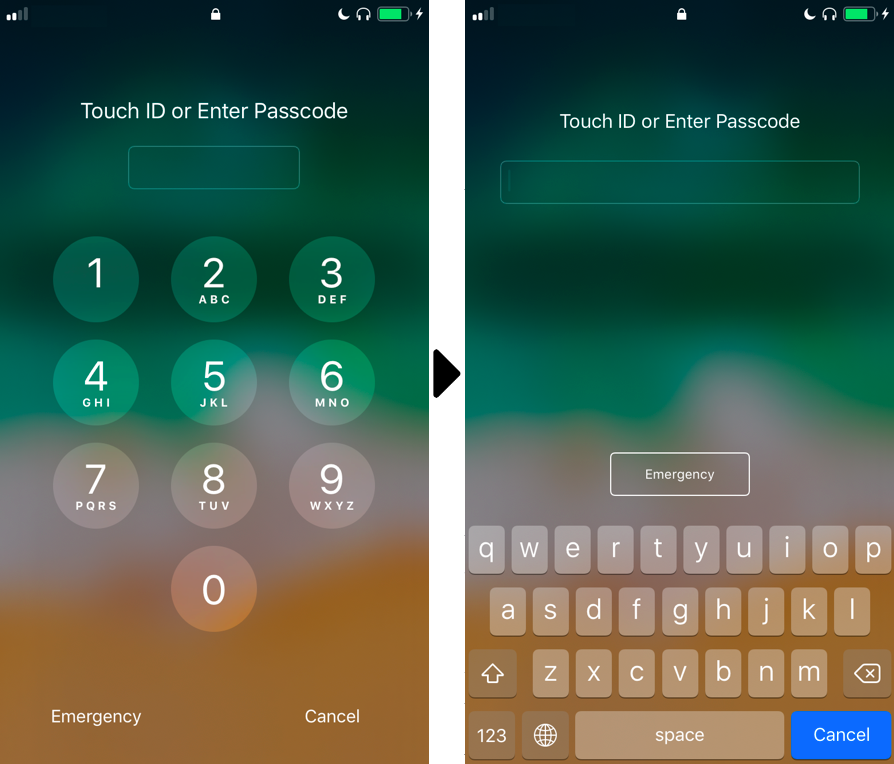
Left: An ordinary numeric passcode unlock page for iPhone. Right: An unlock page for iPhone, with a keyboard including both numbers and letters.
Use an alphanumeric passcode. On mobile devices, you often see numeric (0-9) passcodes, as well as grids. For each of these types of passcodes, you’re left with a relatively small number of possibilities, so using a passcode with both letters and numbers introduces millions of new possible passcodes, making your phone much harder for someone to unlock.
Likewise, consider a passphrase. This could be random, or near-random, words strung together (e.g., “wrench quicksand”). Using unpredictable and, ideally, random words makes unlocking a device much harder. For a concrete way to generate truly random passphrases, check out the Electronic Frontier Foundation’s friendly passphrase generation guide.
The main trade-off with using a more complex password is that it will require slightly more time to type in.
Upgrading your passcode is easy.
Android users: Open Settings app > Security and privacy (this may vary by manufacturer) > Screen Lock
iPhone users: Settings app > “Face ID & Passcode” or “Touch ID and Passcode” > Change Passcode
Thinking through biometrics
The fact is, no one wants to type in their passcode every time, and many phones offer alternative inputs that may or may not be appropriate for your situation, such as the capability to unlock your phone through a fingerprint or a scan of your face with your smartphone camera. These can make it easier to log in and yet, at least in the United States, biometric information such as a fingerprint may have fewer legal protections than a passcode when unlocking your device.
Unlocking a device with biometrics is a decision that will depend on your security needs and the likelihood that it introduces risk for you. Because some situations are more risky than others (e.g., attending a protest versus using your device at home), think about whether unlocking your phone with biometrics is right for you.
Regular maintenance
The importance of regular updates
Every day we hear about new vulnerabilities affecting our apps and devices. But behind the scenes, lone hackers, hacking groups, companies, and government hackers are constantly finding and dissecting vulnerabilities in the software we frequently use, analyzing its weak points, and crafting exploits to manipulate or steal our personal data. In turn, security teams at companies responsible for your operating system, like Google, Microsoft, and Apple, are scrambling every single day to put out these fires. The main way they can help you inoculate your device from vulnerabilities and exploits is through security patches.
Google posts Android Security Bulletins to allow observers to see what goes into each security update. If you want to see what kinds of trash fires Apple is putting out with their most recent updates, you can check it out here. For example, Apple a few years ago patched a FaceTime security bug that allowed users to turn on other FaceTime users’ cameras and microphones. If this sounds like a great time to update your device, keep in mind that similarly unpleasant bugs appear all the time.
Your phone is probably nudging you about new software updates for your apps and for the device itself. The truth is sometimes we treat these updates as something that gets in the way. But exactly the opposite is true; security updates should give us reassurance that our devices are safer, allowing us to focus on the things we care about.
When those update notifications appear, don’t hold off. Take updates seriously. Simply updating your phone’s apps and operating system is the most important step you can take for the safety of your devices and your personal data.
Is an app asking you for reasonable permissions?
Whenever you install an app, it may ask for permission to access information stored on your phone, such as your contact list, or information your phone can collect through sensors, such as your location. Maybe an app is asking for information that makes sense to you (e.g., Instagram asking for your camera). But it can also ask for things it is not entitled to. For example, maybe you just want to check the weather. But does your weather app really need access to your precise location data, down to the street address, to tell you the weather in this region?
Most people probably have an app on their device that’s asking for information it doesn’t need. Consider reviewing the permissions for apps running on your devices, and turning off permissions that make you uncomfortable, or those that don’t seem quite right.
Android users: (it might be slightly different, depending on your version): Open Settings app > Apps & notifications > Advanced > App permissions
iPhone users: Open Settings app > Privacy & Security
Denying a permission could cause an app to function differently or disable some features within that app. For example, if you have the Facebook app installed, you might find that the microphone permission is enabled to allow voice memos. You need to decide whether you’re OK with that. If you never plan on using a feature, there’s no harm in turning off the app’s permissions.
In the future, you should always review app permissions and choose whether to decline to install apps that ask for excessive permissions.
Regularly pruning apps
While you download updates to make it harder for internet strangers to attack your devices, it’s also smart to minimize the number of places that can be attacked in the first place. Security people sometimes call this the attack surface — the range of possible footholds for vulnerabilities, based on issues with the code in the software on your devices.
Because each piece of software increases potential points of vulnerability, you also need to think about what software you don’t need.
If you haven’t used an app for a long time and don’t plan on using it again right away, it may be worthwhile to remove it from your device. Simply removing old, unwanted apps can help make your device much safer.
Extra assurance: Backing up your device
It happens to the best of us: Eventually our devices will be lost, stolen, or broken, and we don’t want to lose access to our data. Every now and again, it’s wise to make a backup copy of mobile files to avoid this cruel fate.
There are free and easy cloud services to help make backups, such as Apple’s iCloud and Google Drive. Each of these options will allow you to use the company’s storage to keep and recover your files. The catch is that, while easy to use, by default we’re also allowing our data to be seen by the company. This leaves the data you back up with a third party open to lawful interception, as well as unlawful access, such as account hacking.
You can defend against lawful and unlawful seizure of data in your mobile cloud backups by pruning sensitive information you aren’t willing to share with a service, and locking down your account with a unique and complex passphrase and two-factor authentication.
Note that Apple users can encrypt backups with iCloud so that even Apple can't read them, but this requires some extra steps to enable.
If the risks involved in backing up with a cloud service are too great, consider backing up your devices locally.
If you have access to an external computer you trust, using it to make local backups will bring you some peace of mind. It’s easy for iPhone users to make backups using the Finder app on a Mac or using iTunes on a PC. Android users with a Windows device can connect their phone to their computer and move the files. For now, the most reliable way to bring files over from an Android device to a Mac is by manually putting files on a USB device, such as a USB thumb drive. You can then move your data onto a longer-term storage option, like your computer and/or an external hard drive.
While you’re at it, it’s also a good idea to back up your computer. Services like Google Drive or Dropbox are convenient but, again, allow the companies to read your data. For remote backups, consider services like Tresorit, which keep your data in an end-to-end encrypted format, meaning the data can only be read on your devices.
Another good option: using an external drive to back up your device. While there are dozens of strong options, Seagate drives are fast and relatively inexpensive for a great deal of storage space.
Get the word out
Security is a team sport. When your device is safer from compromise — protecting the information connected to your friends and colleagues (e.g., personal conversations) — it helps protect them as well. We therefore encourage you to spread the word about mobile maintenance and put together this guide to help make it as easy as possible.

Download the PDF. You can also edit it by making a copy (File > Make a copy…) on Google Slides.
Remix it, print it out, fold it up, and share it widely.
Personal assistance
Mobile devices are increasingly where we socialize and get our work done, so knowing how to choose and maintain these devices matters. You may have some more specific needs and questions on this topic, and we’re always here to help reporters and news organizations around the world. If that sounds like you, contact our trainers for assistance.





