Confidential tip pages are great resources for journalists, making their tip channels available to would-be sources all in one place. While these pages can be found on the websites of many news organizations and even some individual journalists, reporters can do a great deal to gather more tips and better protect sources.

Screenshot from ProPublica’s confidential tip page.
When is a secure tipline needed?
We know that most of the material that filters through newsroom tiplines is noise, and even useful tips are not necessarily sensitive. But occasionally, information shared through tiplines or in conversations with journalists could put sources at risk of retaliation. However, it’s not always apparent when a source or tip is sensitive. We can minimize the risk by taking a more proactive security posture by default, and ensuring sources have the information they need to make an informed decision when reaching out.
Think about who your source is likely to upset by sharing details for a story — maybe their employer or another group they’re affiliated with. If you were to publish information that could link back to this source, ask yourself a few questions:
- What kind of resources might an investigator have to look into the source (e.g., time on their hands, and technical, financial, or legal resources)?
- How likely is it that a would-be investigator actually investigates?
- What are the likely consequences for the source (e.g., a slap on the wrist, excommunication, loss of livelihood)?
If a source has a tip about a small, under-resourced outfit, such as a local restaurant, they can reach out essentially anywhere outside of work with minimal fear of retaliation. However, if the tip concerns a better-resourced investigator, such as a large, famously litigious company, they’ll need to be much more mindful about how to reach out safely.
Just like sending a postcard, the content of any message sent through the web can often be read by intermediaries. Likewise, intermediaries have certain types of information about the message, such as the name and address of the recipient, to ensure it gets to its destination. We call this metadata — information about the conversation, such as who spoke to whom, and when they spoke.
News organizations will typically accept ordinary phone calls, emails, or social media DMs for tips. These channels are fine for many conversations, particularly with sources who offer tips that are not sensitive and whose identities don’t need to be concealed in publication. The issue with using these platforms to gather sensitive or confidential tips is they are not end-to-end encrypted, meaning that the service provider can eavesdrop on the conversation without any issue. Instead, some simple chat tools, like Signal, offer end-to-end encryption to less technologically savvy sources.
However, even end-to-end encryption does not mean the participants in a conversation are anonymous. If someone truly doesn’t want to be recognized in conversation with the newsroom — either by the newsroom itself or intermediary service providers — they need to take extra precautions to be sure they don’t “out” themselves with a trail of metadata.
Metadata is a necessary part of how all messages are delivered on the web. But much like we don’t have to write the return address on an envelope, there are some techniques anyone can use to make metadata less useful to eavesdroppers.
On any tip page, journalists ought to list some baseline precautions. For essentially everyone, this means:
- Don’t reach out from work. Avoid workplace devices, online accounts, or networks.
- Don’t reach out over any channel your employer can likely see, such as Facebook Groups or X.
- Keep your circle small. The fewer people who know about your tipping activities, the better.
Marketing successfully
It might sound obvious, but the secure tip page needs to be widely marketed.
Regularly placing information about tips in social media feeds and print is one way to ensure someone doesn’t have to look hard for this information. This also minimizes the risk to sources. When, without conscious effort, anyone can stumble over information about how to reach out to your organization, would-be sources have much more plausible deniability.
Think about it: If your source isn’t searching for tip pages, they can leave behind fewer digital breadcrumbs, such as browser history, connection logs stored by the internet service provider, or websites visited along the way (e.g., by googling the tip page). Advertising widely has clear benefits to both the newsroom and would-be sources.

For example, The New York Times regularly posts links to its tip page, and its profile on X includes a link to its tip page. The social media platform may log who clicked on the link, but this approach introduces more plausible deniability.
Print media should also proactively advertise confidential tip channels. For example, The Globe and Mail advertises its SecureDrop on the front page of its print edition.

This also matters for getting unfamiliar sources to contact you from safer channels the very first time they reach out. Why does this matter? Conversations with sources can quickly move from mundane to sensitive, and it’s generally easier for everyone to have chosen reasonably safe channels from the outset. When you don’t, it makes safe conversations with some of your most interesting sources much more complicated.

The web address format matters
When it comes to your readers’ privacy, there’s a big difference between tips.nytimes.com and nytimes.com/tips. One introduces needless risk to readers, while the other is benign. What’s the big deal?
Most modern news websites now offer HTTPS (e.g., https://freedom.press), which helps secure users’ browsing traffic between their computer and the website itself. However, the fact that someone visited an HTTPS website is still visible to intermediaries, such as internet service providers like Comcast or Verizon. How’s this possible?
When you connect to a website, something called the Domain Name Service is working in the background to ensure that the name you type in (e.g., https://freedom.press) will automatically connect to a number (e.g., 172.67.6.99) associated with the server where the website is hosted. In the course of connecting, the DNS needs to see the domain name the user is trying to access. ISPs provide the DNS for their customers and can therefore see what websites users connect to.
To the ISP, DNS requests to subdomains (e.g., tips.nytimes.com) look different than domain names (e.g., nytimes.com). That’s why there’s a big difference between tips.nytimes.com and nytimes.com/tips — while the first web address reveals this request is directed to the tip section of the media organization’s website, the second reveals that someone is requesting something on nytimes.com. The first URL signals the reader is potentially curious about sending a tip, but the second looks like a simple website visit.
The short version: To better protect would-be sources, news organizations should place tip pages on their website’s subdirectory (e.g., nytimes.com/tips), rather than create a subdomain for tips.
Speaking to the tradeoffs
While you don’t want to scare folks away, it’s important to share the properties of the communication channels you support to ensure sources are reaching out safely. In practice, this means describing the advantages and disadvantages of each channel as concisely as possible.
Newsrooms commonly support a handful of tools that help facilitate private conversations and can obscure the identity of the sender. These tools include encrypted messaging apps such as Signal, secure emails with PGP encryption, web forms, postal mail, and the whistleblowing submission system SecureDrop. To ensure sources reach out safely, it’s necessary to outline some of the benefits and trade-offs of these channels.
Signal
Why Signal?
Signal is a free and open source encrypted messaging app for Android and iOS. Signal supports end-to-end encryption for text messages, and voice and video calls. It also has a convenient “disappearing messages” feature that allows for messages in a conversation to self-destruct after a set amount of time, from seconds to weeks. Signal is considered one of the most secure messaging apps in widespread use and is designed to keep as little user data as possible.
What are the trade-offs?
While Signal retains nearly no metadata and provides some powerful techniques for obscuring the participants in conversation, secure tip pages should note that Signal is not designed to facilitate complete anonymity.
Signal gives users the option to enable usernames. If sources do not want to share their personal phone number with media organizations, they should enable a username before reaching out.
For media organizations that have not yet enabled a Signal username, it’s important to understand that sources can also inadvertently put your organization’s phone number in their phone’s contact list. In some situations, this may place them at risk if their device is ever seized or if their contact list is uploaded to a cloud service provider like Google Drive or iCloud. This is also a good reason for newsrooms to consider using Signal usernames by default. Consider the example from KQED California Newsroom, which shares a username and a QR code generated by Signal, instead of a phone number.
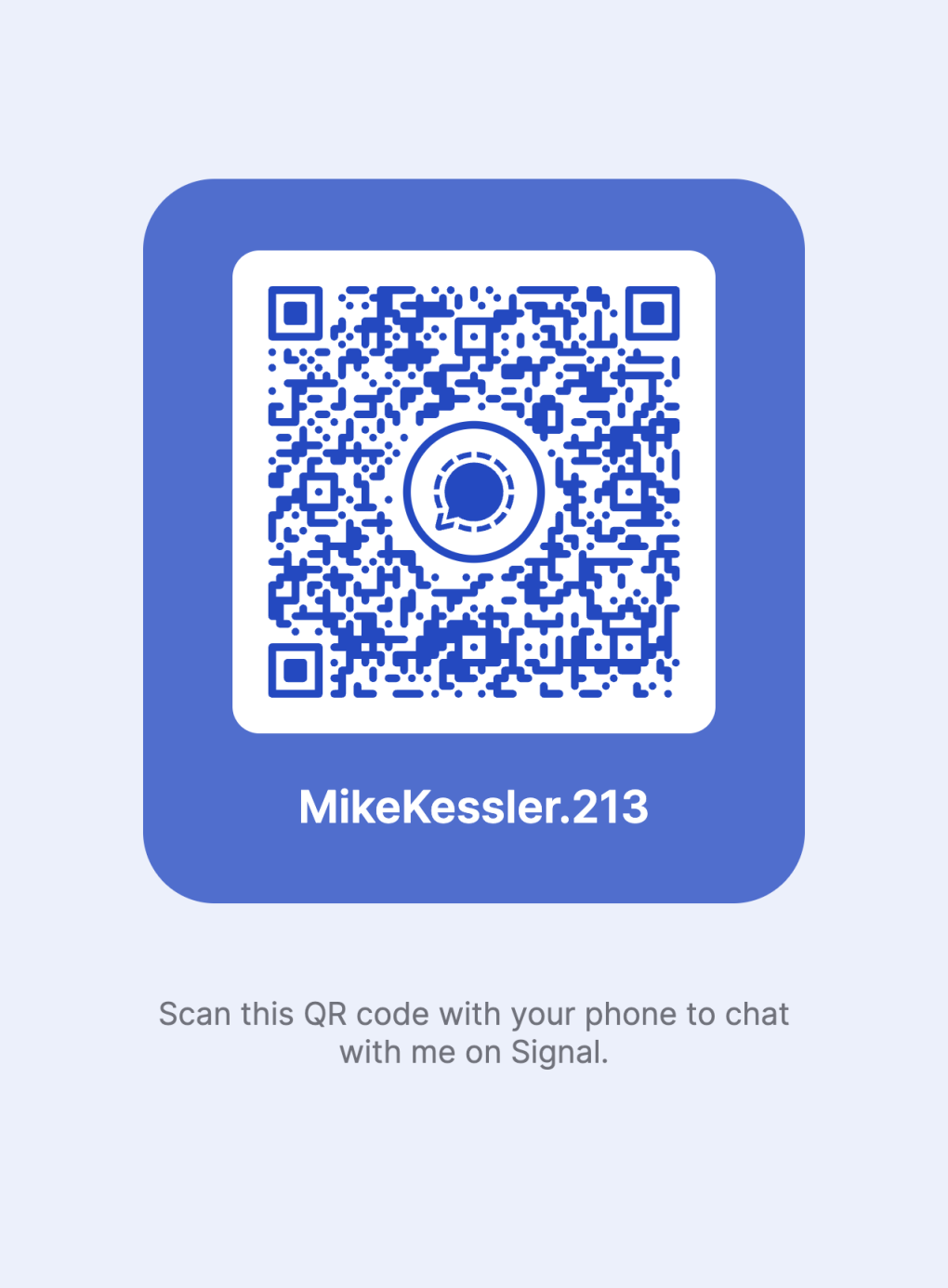
A username and QR code generated by Signal, via KQED California Newsroom.
Encrypted email, with PGP
Why PGP?
Email is a lot like sending a postcard: Anyone who picks it up along the way can give the message a read. It takes some getting used to, but PGP, or Pretty Good Privacy, can help address this problem.
PGP allows users to encrypt messages and files to specified recipients. While it can be used to send encrypted messages over other channels, it’s most commonly used over email. Users generate a public key, a file that can be used to encrypt messages and can be shared publicly, and a private key, a file used to decrypt messages and that must be kept secret. This arrangement allows savvy users to email newsrooms securely.
Speaking to the tradeoffs
While PGP can be used over other channels, news organizations accept PGP primarily over email. This means all of the usual issues with email persist: The participants in conversation are visible to the email service providers and some intermediaries. News organizations should therefore warn users that PGP email subject lines and the identities of the users in conversation are not end-to-end encrypted. Users should also consider using a new email that is separate from their persistent identity.
Likewise, it might be worthwhile to simply caution unfamiliar users that PGP requires some technical know-how.
Web forms
Why web forms?
Some organizations, including ProPublica and The New York Times, offer forms built into their tip page to allow users to submit tips. Because most standard web connections are secured with HTTPS, this can be a simple and relatively secure way to submit tips.
What are the trade-offs?
The main issue with web forms is how the newsroom chooses to store them. These tips can go directly into a secure server, but if the server is compromised or controlled by a third party, we can’t guarantee confidentiality for anyone who visits the website, including those who shared a tip. The onus is on newsrooms to manage their servers and data pipelines securely and confidentially.
Postal mail
Why postal mail?
Sending in physical mail can be a convenient and low-tech way to share documents, or even media, with newsrooms (e.g., over a small USB device or SD card). Postal mail also has a somewhat unique advantage: It doesn’t necessarily require the sender to identify themselves.
What are the trade-offs?
In the U.S., the main issue with postal mail is that the Postal Service scans each parcel’s exterior. If sources are concerned about protecting their identity, secure tip pages should include warnings not to use a return address on the envelope. Sources can still keep their contact details inside the envelope for continued correspondence.
Because the location of each parcel is so closely monitored, sources may want to use a postal drop-off point that they don’t use every day. Newsrooms should also be aware that printed workplace materials may also be risky to share in print, as many printers will stamp paper with nearly-invisible tracking dots, which can be used to identify documents and print dates. (See The Intercept’s tip page for suggested language.)
SecureDrop
Why SecureDrop?
Unlike other digital tip channels, SecureDrop is designed to support source anonymity by default. By encrypting and tunneling traffic over the Tor anonymity network, newsrooms can host a secure dropbox. Any tips sent to this dropbox can only be decrypted on a special, hardened machine that is disconnected from the web. This allows sources to reach out anonymously with fairly little effort, while the newsroom isolates potentially dangerous software on its “offline” computer.
What are the trade-offs?
Sources should know that when using SecureDrop, the ISP — such as Comcast — can’t tell what they’re doing, but they can still tell they’re using Tor. This might be a problem if you are connecting from a network where Tor traffic draws suspicion from the network administrator or the local government. (For example, in some countries, there are few users making connections over Tor, which could call unwanted attention to those users.)
To maintain real anonymity, sources should also take care to remove metadata from any documents they submit — for example, by taking a screenshot of a document and sharing the screenshot, rather than sharing the original document. Read this, or reach out to Freedom of the Press Foundation (FPF) to learn more about metadata redaction techniques.
Safeguard sources while getting stories
Speaking about the trade-offs of each channel is a great way to demonstrate that the newsroom takes tips seriously, and in turn, reassures sources about their relative safety when reaching out. Likewise, we know sources will reach out over channels that are not necessarily safe or appropriate for the information that they’d like to share. Advertising your channels widely, along with their trade-offs, will invite more tips, help sources build confidence that they’re reaching out over appropriate channels, and help journalists accept more tips with relative safety.
Read more about how to minimize risk to sources reaching out through secure tip pages. You can also reach out to our Digital Security Training team to learn more about building secure tip pages or for assistance setting up tiplines.