Your team can do wonders to protect yourselves and your data by requiring a second piece of information beyond your password when logging in. We call this two-factor authentication (2FA). Once you’ve enabled 2FA on an account, you’ll be asked to enter both your password and a second piece of information.This second piece of information typically comes in the form of a temporary code (e.g., 422367) accessible only through a device in your possession, like your phone. We love 2FA because it’s one of the most effective ways that we can protect ourselves and our colleagues in the newsroom.
But 2FA also introduces some novel challenges. Many news organizations are now highly distributed, and share their accounts with colleagues who may not have access to the same device. What if you want to use 2FA while sharing an account with someone else? You can optionally store 2FA codes in the cloud to make them accessible to multiple devices, and anyone on the team, but this may introduce novel security risks. This is a tricky decision.
As journalists work from home and need remote access to accounts, we want to talk about some of the options for accessing 2FA codes locally and remotely, and some of their trade-offs. We will assume passing familiarity with how to access an account with temporary 2FA codes. If this doesn’t sound familiar, we have a starter guide for you.
Storing 2FA codes on-device: Less pleasant, but a little more secure
2FA takes many forms, but it most commonly requires something in your possession, such as your phone, or an authentication app. Apps like Google Authenticator and FreeOTP will help you generate and keep track of those temporary 2FA codes for each of your accounts, so that only you (or whoever grabs your phone) can access them.
But let’s say your phone is lost or stolen. You’ll need to manually re-register 2FA for every account on your new device. Depending on how many accounts you have, this can be a labor-intensive process. If you’ve lost your phone, you may be completely locked out of your accounts, requiring you to speak to customer service representatives and prove you are the rightful owner of the account to regain access.
(Fortunately, if you are upgrading your phone and you have access to both phones, Google Authenticator will now allow you to export your 2FA codes to the new device. You can now also back up previously saved 2FA codes from your Google account; this is a big time saver.)
When using a personal device to locally store 2FA codes, the fact that it’s tough to access them remotely is overall good for the security of your account. No one (not even you!) will have an easy time getting into your account without your 2FA device. But if you ever lose track of your personal device, or need to migrate to a new one, recovering is rough.
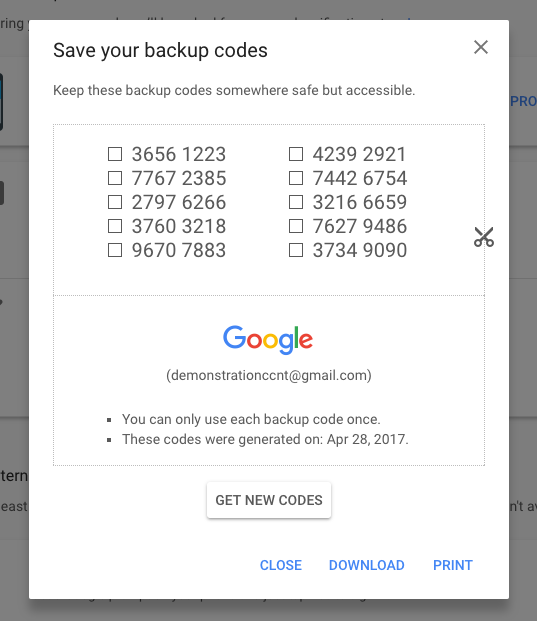
A screenshot of Google's 2FA backup codes.
Many services allow users to generate backup codes — short, persistent alphanumeric codes that will help you log in even if you lose access to your 2FA device. Typically you’ll want to print them out, or keep them somewhere safe with an encrypted backup service that you trust. When storing 2FA credentials on your local device, backup codes are the main way to recover your accounts if your 2FA device is lost or stolen.
Full disclosure: After losing a phone and breaking another, I’ve spent dozens of hours of my life migrating 2FA codes between devices. To get back into my accounts, I’ve also had to prove to many customer service representatives that I am me. It’s good for my security, sure, but it’s not fun. I keep copies of my backup codes to spare my future self this fate.
Storing 2FA codes only on your device is a conservative choice with some meaningful usability tradeoffs. Local authenticator apps also introduce challenges for teams that want shared access to those codes. What if you don’t have direct access to the 2FA device necessary to get into an account you share with others?
That brings us to the benefits and trade-offs of cloud-based 2FA services.
Storing 2FA codes remotely: Better experience, though doing it securely is more complex
Just as you can register 2FA with a local device to generate codes, you can do the same thing with remote services.
Some 2FA services (e.g., Authy) will store your codes in an online account, allowing you to access them both on your phone or other websites. Likewise, a growing number of password management tools (e.g., 1Password, DashLane) will also allow users to store their 2FA codes on multiple devices, and even set up team accounts to share both passwords and 2FA codes within the organization. Your credentials are stored in an encrypted format, so they can only be read on your teams’ devices.
Remote access to 2FA codes is a much better experience than storing codes on one device. If you ever lose access to your phone, or if you happen to upgrade to another phone, no problem. You can just log into your remote 2FA solution and access your codes again. You’re immediately up and running.
The catch is you’re no longer the only one who has access. If someone can hijack your 2FA solution, they can now also hijack your 2FA codes, so it’s really important to lock it down as appropriate for your situation.

A screenshot of Authy, showing a 2FA code for an app.
For example, Authy allows users to conveniently store their 2FA codes in the cloud. Users can register new devices by using a confirmation code sent to their phone number through a text message or phone call. Most of the time, this is a sensible way to confirm that you own the phone, but because our cellphone infrastructure is radically insecure, it’s possible for hackers to intercept these confirmation codes and register their own device to your account, giving them access to your 2FA codes. Indeed, these phone hijacking attacks are becoming quite common.
Authy offers some thoughtful features for preventing unwanted device registrations on your account, but they’ve chosen not to enable these features by default. There’s a reasonable security and usability trade-off at work here: Most people are more likely to lose access to a phone and accidentally lock themselves out of their 2FA-enabled accounts than to have their phone number hijacked.
At the same time, journalists are also at higher risk than the general public.
For many, the convenience of being able to access your 2FA codes from any device at any time, and extend that access to your teammates, may be a worthy trade-off. But if your organization has experienced highly targeted attacks, it’s worthwhile to dig into Authy’s documentation to learn how to tighten security settings beyond the defaults, or simply keep your 2FA codes locally on one device.
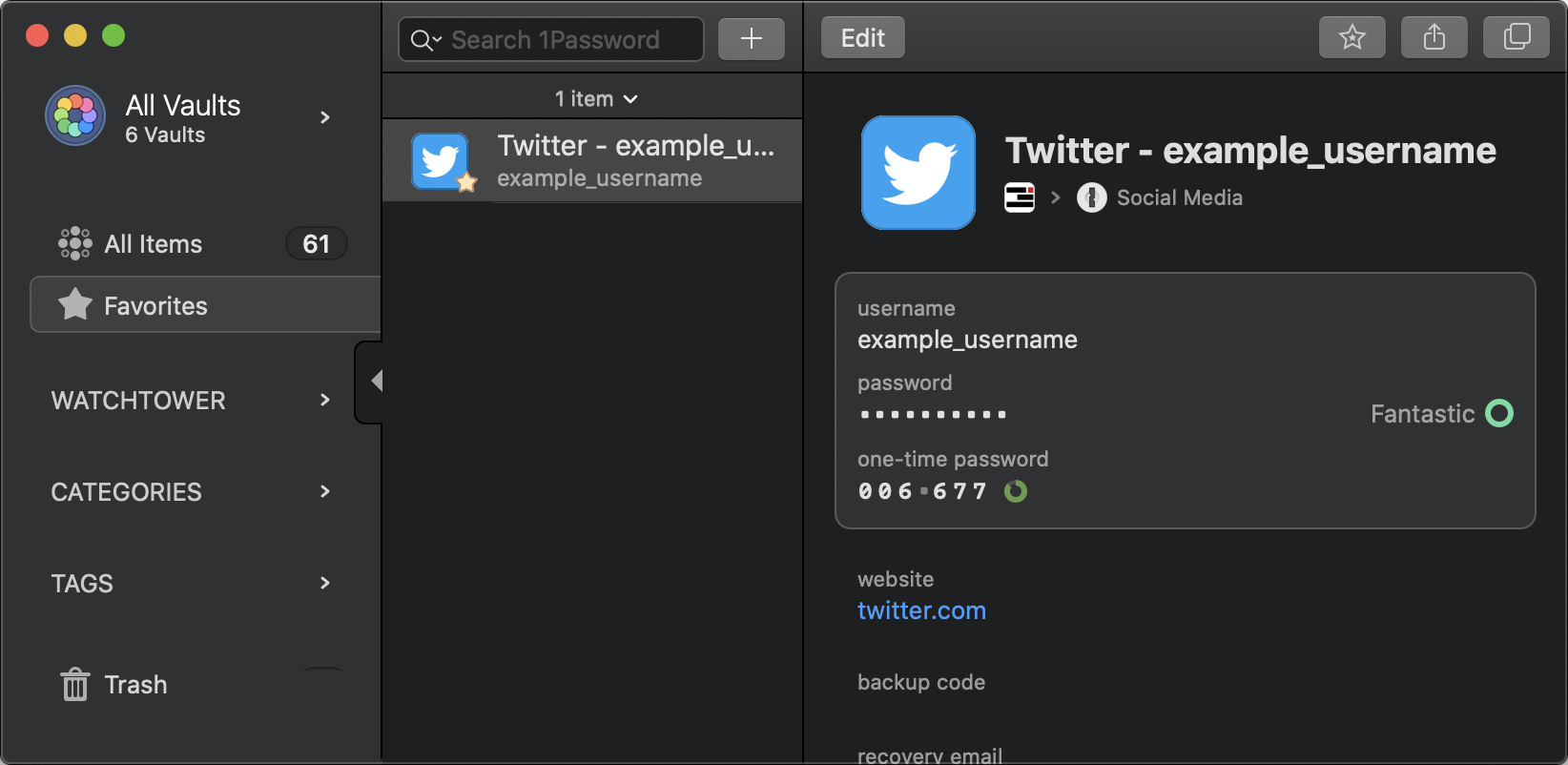
A screenshot of 2FA codes stored in 1Password.
Likewise, a growing number of password managers also offer integrated 2FA support. This can be a convenient way for teams to access their 2FA codes from anywhere.
Security geeks have many feelings about whether it’s a good idea to put 2FA codes in a password manager. When centralizing all of your passwords and 2FA codes into one place, you only need to unlock the password manager’s vault to get all of the credentials.
At the same time, breaking into a password manager like 1Password or DashLane is not trivial. Under normal circumstances, accessing a password manager requires a few pieces of information from someone with existing access. For example, when an unregistered user tries to access 1Password, they need to provide a confirmation email, and the Secret Key for the account — essentially a code to unscramble the encrypted password manager vault, making it legible on their device. Finally, they need the vault’s password to actually log in and read the 2FA codes.
Given the controls built into contemporary password managers, if someone has remote access to your team’s password manager, chances are you’ve got broader underlying security issues to fix.
Just like any piece of software, it’s only as secure as the operating system where it resides (e.g., Windows, macOS). If an attacker manages to plant malware on your device, giving them a beachhead to the operating system itself, the security guarantees of a password manager largely go out the window. The best defense against attacks on the operating system are regular old security updates, and this is why it’s so important to install security updates as soon as they are available.
With regular updates and use of a password manager, stealing 2FA codes is a difficult (but not impossible) task. If you’re not staying updated, your local 2FA app (e.g., Google Authenticator) is just as vulnerable as any piece of software on your phone.
Storing 2FA codes in the cloud is a convenient option that may make your team’s lives easier. For most people it’s a great choice. But because news institutions are some of the most highly-targeted organizations in the world, it’s a choice worth considering seriously. If you’re dealing with a person, or group with a vendetta against your organization, it might be worthwhile to have a discussion about risk with your team, and when to store 2FA codes locally or in the cloud.
What’s right for you and your team?
Whether your team chooses to store 2FA codes locally or remotely, and where, depends on your particular concerns. Both simplicity and safety matter. When considering how your team can most practically and safely use 2FA in a way that works for you, ask yourselves some questions:
- Is it important for more than one person to have regular access to the account?
- Would it be a significant burden if you needed to incorporate a new device into your workflow?
- How many people (and their corresponding devices) should have access?
- What strategies do you have in place to ensure the device is up-to-date?
- What accounts, and how many are you making remotely accessible?
- Has your organization already suffered attacks on staff accounts? How likely do you think that is with a remote 2FA option?
- If you use a remote option, what kind of controls (if any) does it have in place to prevent someone from requesting access from a new device?
- If you use a remote storage option and it can’t prevent someone from requesting access, how would someone request access in the first place (e.g., email, a phone number)? What protections do you have in place to prevent those channels from being hijacked?
Don’t hesitate to reach out for help. Our digital security training team is always ready to assist news organizations in thinking through, and implementing a strong authentication posture for your online accounts. Be safe out there.




