A United States Parks Police officer records the crowd during a protest around the 2017 presidential inauguration of Donald Trump in Washington, D.C. Following the steps in our guide is the first step toward protecting your reporting data at high-risk moments like these. Photo by Mobilus In Mobili. CC BY-SA 2.0
As journalists contend with increasingly violent rhetoric and threats, they’re also seeking more support in fighting online harassment and doxxing. In fact, it’s now one of the most sought-after training topics from our Digital Security Training team. We’re also asked for guidance around protecting data, sources, and colleagues from escalating digital security threats both in the field and at home, with more media professionals working remotely.
Here, we’ve gathered resources that build digital security skills for all journalists, regardless of the sensitivity of their work. Of course, recommendations may shift to adapt to changes in technology and laws impacting it, and we suggest checking our Guides & Training resources often.
Table of contents:
- Start with a risk assessment
- Concerned about account hacking? Use a password manager and two-factor authentication.
- Take care of your computer. Run your updates and protect data on your devices with encryption.
- Boost the security and privacy of your mobile phone with a few tweaks.
- Surfing the web or researching a story: Create a privacy and security toolkit for all your browsing
- End-to-end encrypt your comms whenever possible
- Learn how to mitigate and respond to online harassment
- Reach out when you need help
Start with a risk assessment
Protecting your valuable data is an ever-evolving process. As your priorities and resources change, so, too, should your digital security plan. A risk assessment provides a simple framework to identify the threats to your data security so you can customize your defensive strategy.
The bottom line: Design a plan based on your needs
- Conduct a risk assessment: Base your digital security plan on your needs and concerns, so that you respond to the most immediate threats to you. Here's a risk assessment exercise from the Electronic Frontier Foundation.
Concerned about account hacking? Use a password manager and two-factor authentication.
Think of all the valuable data you store within online accounts: email, contacts, transcripts, cloud storage, device backups, and private messages in social media. It's a vast data ecosystem, and for journalists, it's one that requires extra care to make sure no third party can easily access it.
Check haveibeenpwned.com to see if your information has been involved in a recent data breach. Rotate any breached passwords, and don't reuse them on any other services.
A password manager is a tool that assists you in making strong and unique passwords for all your accounts so they cannot be easily guessed by a hacker. A password manager stores your passwords securely in an encrypted database, unlocked with one password that only you know.
Two-factor authentication is the other half of your account security solution. With 2FA enabled on an account, you'll be asked to enter a second method of authentication (typically a short numeric code) after your password. Only you have physical access to this second method of authentication, either through your phone or another piece of hardware.
The bottom line: Account security
- Use a password manager: Online password managers Bitwarden and 1Password are user-friendly tools best for users who need a convenient password management solution. Users who prefer to keep their credentials offline can use the free and open source tool KeepassXC. Learn how to choose the best password manager for your needs.
- Enable 2FA: Get guidance on enabling 2FA on your accounts at 2fa.directory. While 2FA over SMS text messages is better than nothing, whenever possible opt for app-based options Google Authenticator or FreeOTP, which can deliver your one-time login codes more safely. With a track record as the most secure 2FA option, hardware-based solutions like a YubiKey can be used on a growing number of popular services.
- Don't get phished: Follow the recommendations in our phishing prevention guide, and spread anti-phishing tips across your organization. Share the information your teammates need to avoid being the “weakest link”.
Take care of your computer. Run your updates and protect data on your devices with encryption.
Your devices are your gateway to the tools you need to get your work done. Software updates keep your operating system and the software you download running smoothly, and they often contain patches to vulnerabilities bad actors may try to exploit with malware.
Another simple way to harden your devices is to make sure you've enabled full disk encryption. Full disk encryption is a utility that scrambles all the data stored on your device as soon as you power it down. This means your data is rendered unreadable to anyone without your encryption key (typically unlocked with a password or passcode). If you store sensitive data on your device, especially if you bring your devices with you into the field, full disk encryption is essential.
The bottom line: Desktop security
- Keep your desktop operating system and apps up to date: While you're at it, enable automatic updates whenever possible.
- Enable full disk encryption on your computer: If you have a Mac, enable FileVault. If you’re on a PC running Windows, enable BitLocker. Not all versions of Windows support Bitlocker, so check if your version supports it.
Boost the security and privacy of your mobile phone with a few tweaks.
Many journalists rely on their phones for core aspects of their newsgathering. However, sometimes apps erode user privacy by requesting unnecessary access to location data, your contact list, the clipboard, and so on. To make your phone safer for work, check your app permissions and dial the intrusive apps back.

2019 research published by security firm Avast lists some of the dubious app permissions requested by "flashlight apps" in the Google Play Store. Image: avast.io.
While you're there, make note of any apps that require suspicious levels of access to your personal data (like a flashlight app with permissions to record your calls) and, well, delete them immediately! These apps make money by selling your data to ad networks and, in some cases, companies under U.S. government contracts.
The bottom line: Mobile security
- Keep your mobile operating system and apps up to date: Enable automatic updates to keep you on track.
- Enable full disk encryption on your mobile phone: iOS devices are full disk encrypted by default, so iPhone users are already covered. Most modern, up-to-date Android devices will also have disk encryption enabled by default. If you have an older device, you'll want to enable it by looking for “full disk encryption,” “file-based encryption,” or a similar variant in your security settings.
- Review your app permissions:
- Android users (it might be slightly different, depending on your version): Open Settings app > Apps & notifications > Advanced > App permissions
- iPhone users: Open Settings app > Privacy & Security
Surfing the web or researching a story: Create a privacy and security toolkit for all your browsing
First, let's discuss which browser is right for your everyday browsing. Security-focused Chrome and privacy-respecting Firefox are two of the most popular browsers on the market. There's also Brave, which is based on Chrome's code, and has additional built-in privacy features. If you want to compare the privacy and security benefits of popular browsers supported on all major platforms, check out our guide to choosing a web browser.
Next, what should you add to your toolkit for riskier browsing and research? When you don't trust the owner of the website you're investigating, you'll want to power on a Virtual Private Network before you start browsing. A VPN will allow you to access websites without revealing your IP address, which may be associated with your approximate location.
With a VPN, you will appear as though you’re visiting from a remote server controlled by your VPN provider, possibly somewhere quite far away from you. Check out our guide to choosing a VPN.
The bottom line: Browsing privacy and security toolkit
- Tweak your browser's privacy and security settings: Consumer Reports' Security Planner guides you to where you can adjust your settings in any recommended browser. As a start, we recommend disabling third party cookies, and reviewing when your browser can access your camera and microphone. If you'd like to be warned before visiting a site that doesn't support secure connections, you can enable HTTPS-only mode in your browser's security settings.
- Block trackers and ads: Privacy Badger is a powerful tracker blocker, and works well in tandem with an ad blocker like uBlock Origin (you can always make exceptions for your favorite news orgs that rely on ad revenue).
- Choose the right VPN for you: Invest in a trustworthy VPN provider. Read our guide to learn about technical and policy standards to look for in a more trustworthy VPN. If you already have some background on this topic, you can jump to our shortlist. For more guidance, Wirecutter also has a solid framework for determining its recommended VPNs.
End-to-end encrypt your comms whenever possible
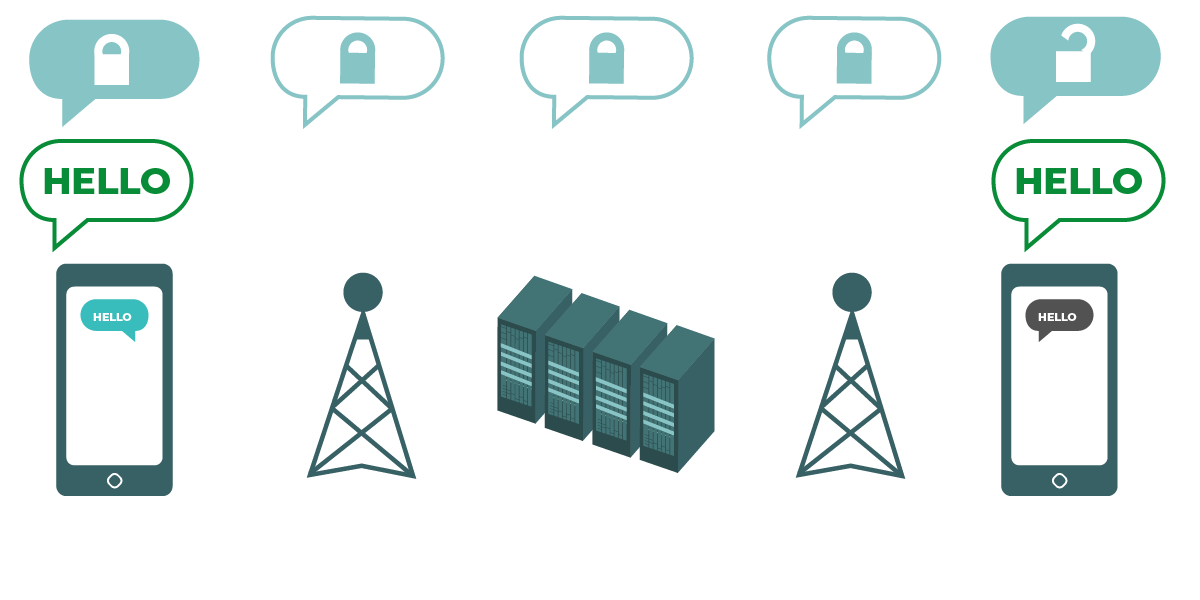
When communicating over an end-to-end encrypted channel, neither the service provider nor eavesdroppers can read your message content. Image by the Electronic Frontier Foundation via Surveillance Self-Defense. CC BY
Between connecting with sources and discussing active investigations with colleagues, journalists need secure and private platforms for sensitive conversations. When a conversation covers sensitive topics, use end-to-end encryption to ensure that only you and your intended recipients have access to the content of your conversation.
There are a number of end-to-end encrypted platforms out there for secure messaging, voice calls, and video conferencing. No one platform is exactly the same in its implementation of end-to-end encryption. We recommend comparing apps based on how they handle conversation metadata (e.g., does the platform have access to my contact list? Can they keep track of who messages me, and when?) and their relative levels of accessibility (e.g., can my conversation partner download and make use of this app?).
The bottom line: Communication security
- Call and message securely: Use Signal for end-to-end encrypted messaging, voice and video calls. WhatsApp is a popular alternative with end-to-end encryption and support for group calls, however, WhatsApp's parent company, Meta, is much more nosy about your usage metadata. Read our beginner- and security-focused guides for Signal. WhatsApp users can follow our guide on upgrading its security.
- Use a secure video conferencing platform: There's a lot of competition in the video conferencing space, so we recommend starting with our overview. Zoom rolled out end-to-end encryption for all users, but you'll have to enable it in your settings first. Jitsi Meet, a free service for ephemeral meeting rooms, also supports end-to-end encryption for those users that enable it at the start of the meeting.
Learn how to mitigate and respond to online harassment
Online harassment takes many forms. Doxxing (collecting a target's personal information and publishing it) and trolling (spouting abusive language and mockery about a target on a public forum) are among the types of online attacks aimed at journalists.
We're seeing online harassment used as a tactic to suppress journalists with growing frequency. Research into online harassment suggests that some reporters are more likely to be targeted based on their gender, sexual orientation, or ethnic background. We recommend that all journalists learn to anticipate the damage online harassment attacks might cause, and how to thoughtfully create a response plan before an incident occurs to help minimize it.
The bottom line: Online harassment prevention and response
- Read our collection of resources from industry experts on online harassment mitigation and response: Whether you're looking for preventative tips, recommendations for psychosocial care, or incident response, you can turn to our curated resources for guides and services from PEN America, International Women's Media Foundation, and The New York Times, among others.
Reach out when you need help
There's targeted support out there for journalists in need. FPF has developed resources to support journalists’ quickly-changing digital security needs, including for login security with passkeys, securing your home WiFi, and videoconferencing. Access Now maintains a 24/7 digital security helpline for journalists and other at-risk communities.
If you are a journalist or newsroom in a specialized situation that needs additional digital security support, reach out! Our digital security team provides consulting and training services, priced at a sliding scale.